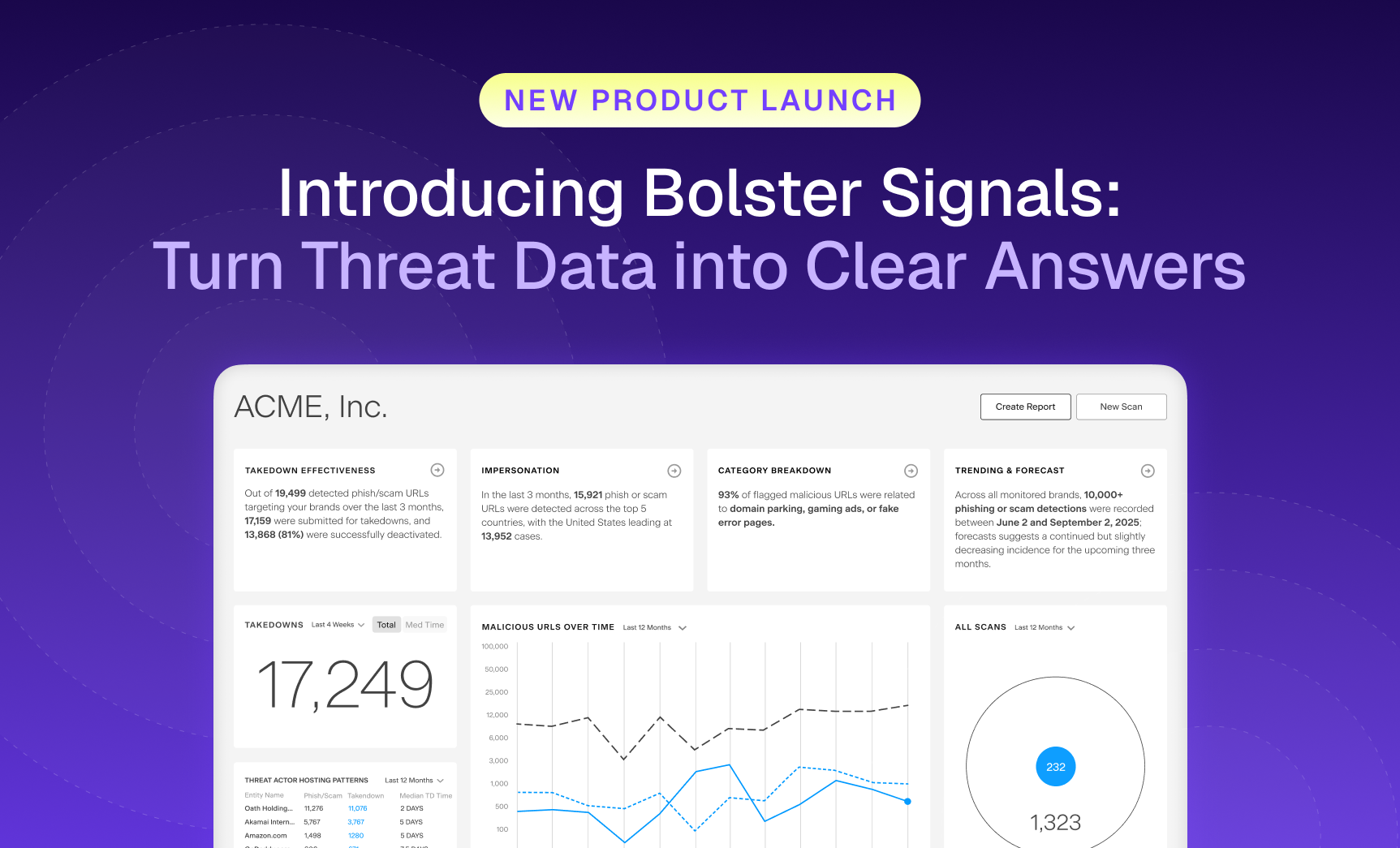
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
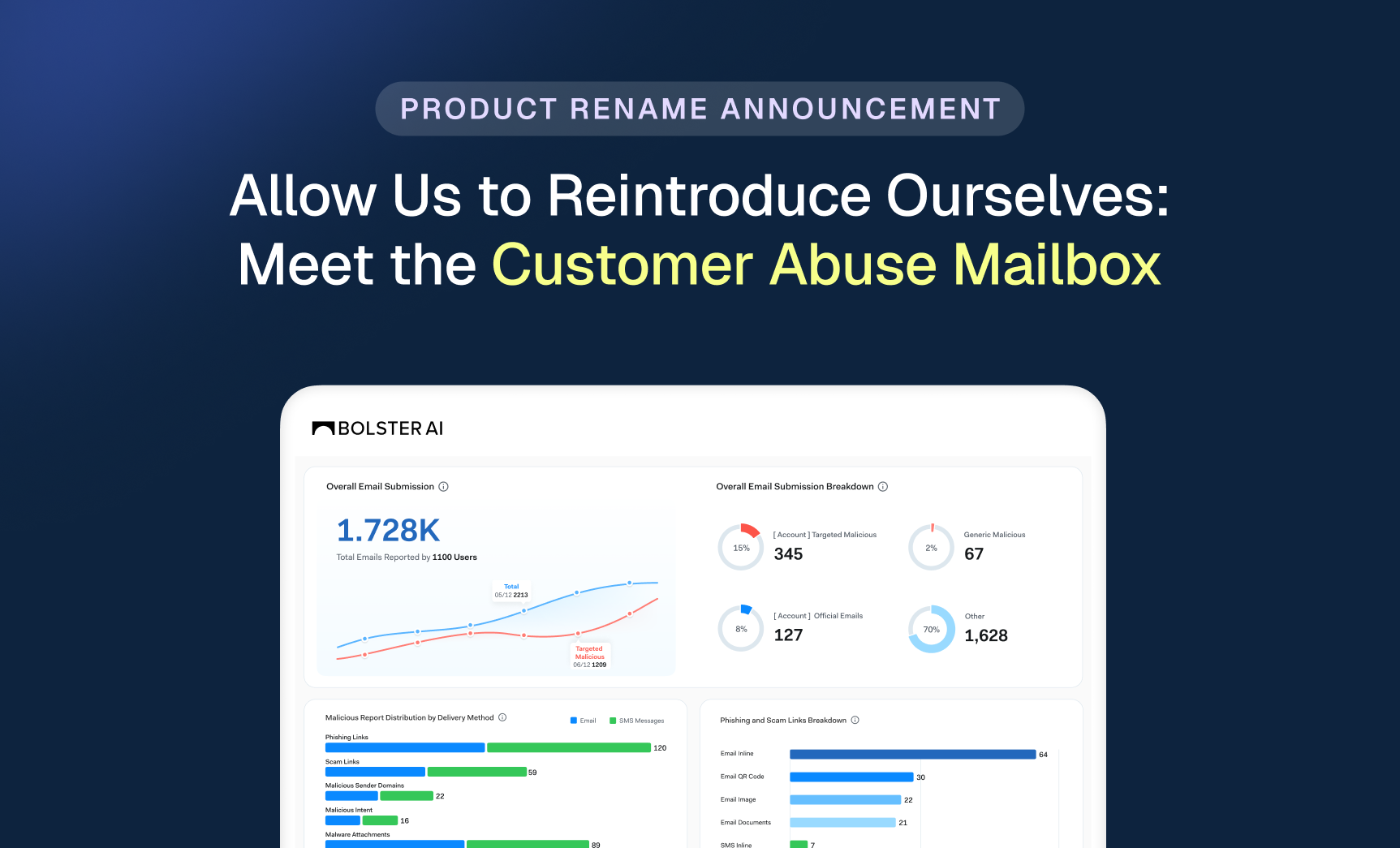
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
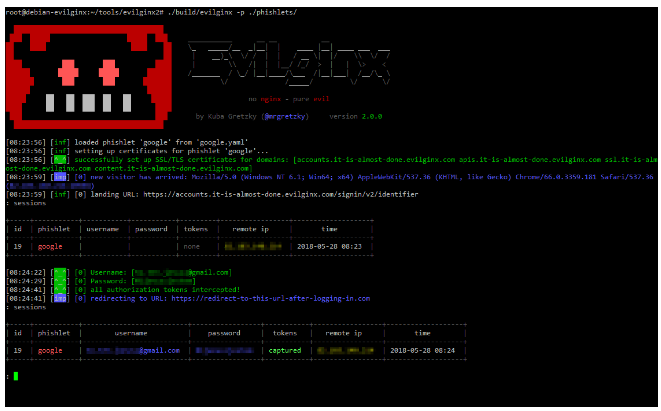
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page.…
Holiday Fraud is Exploding: Here Are the 7 Scams Hitting Consumers Now
Spoiler: They’re more sophisticated, more convincing, and harder to spot than ever. …
Swapzone "Profit Trick" Web-Inject: From Lure to Live DOM Hijack
Introduction At Bolster’s Threat Intelligence Lab, we recently investigated a…
Conditional Phishing and Beyond: The Hidden Triggers in Modern Cyber Attacks
Introduction Phishing has always been about deception, but in recent…
Image Tokenization: How Vision Transformers See the World
Convolutional Neural Networks (CNNs) have dominated computer vision for the…
The ROI of Brand Protection: Why Safeguarding Your Brand Pays Off
Brand abuse isn’t just a nuisance—it’s a threat to your…
Quantum Computing and the Future of Hosting: Why It's Time to Prepare Now
Google, AWS, and IBM aren’t just dabbling in quantum—they’re investing…
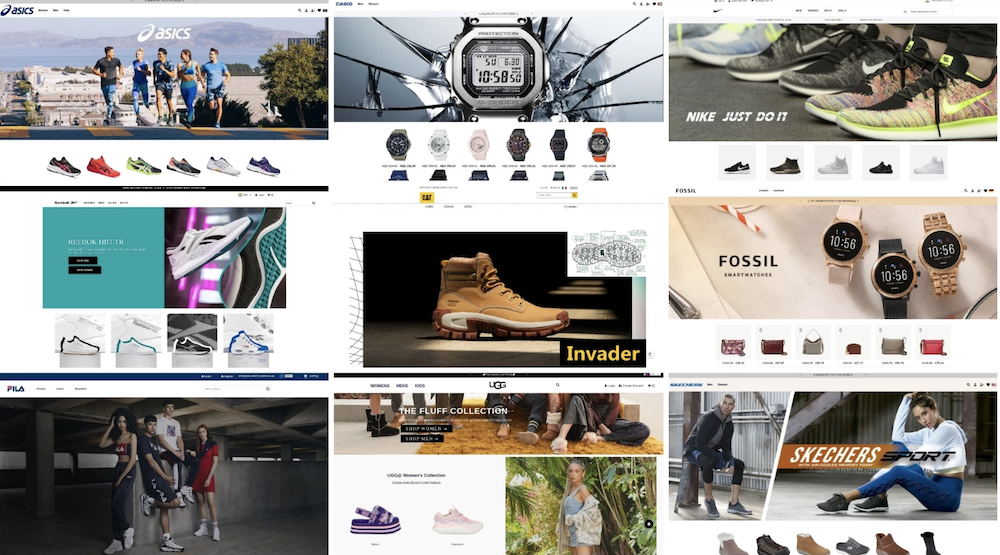
How a Massive Brand Impersonation Scam Campaign Targeted Popular Apparel Brands
Back in 2023, Bolster’s threat research team uncovered a widespread…
Large Language Models for Cybersecurity: The Role of LLMs in Threat Hunting
Organizations are turning to artificial intelligence (AI) and, more specifically,…
Social Engineering: The Gateway to Phishing Attacks
Cybersecurity threats are constant, and social engineering is one of…
AI's influence on stock market predictions & using AI in your investing strategy
Artificial intelligence has found its place in financial markets, bringing…