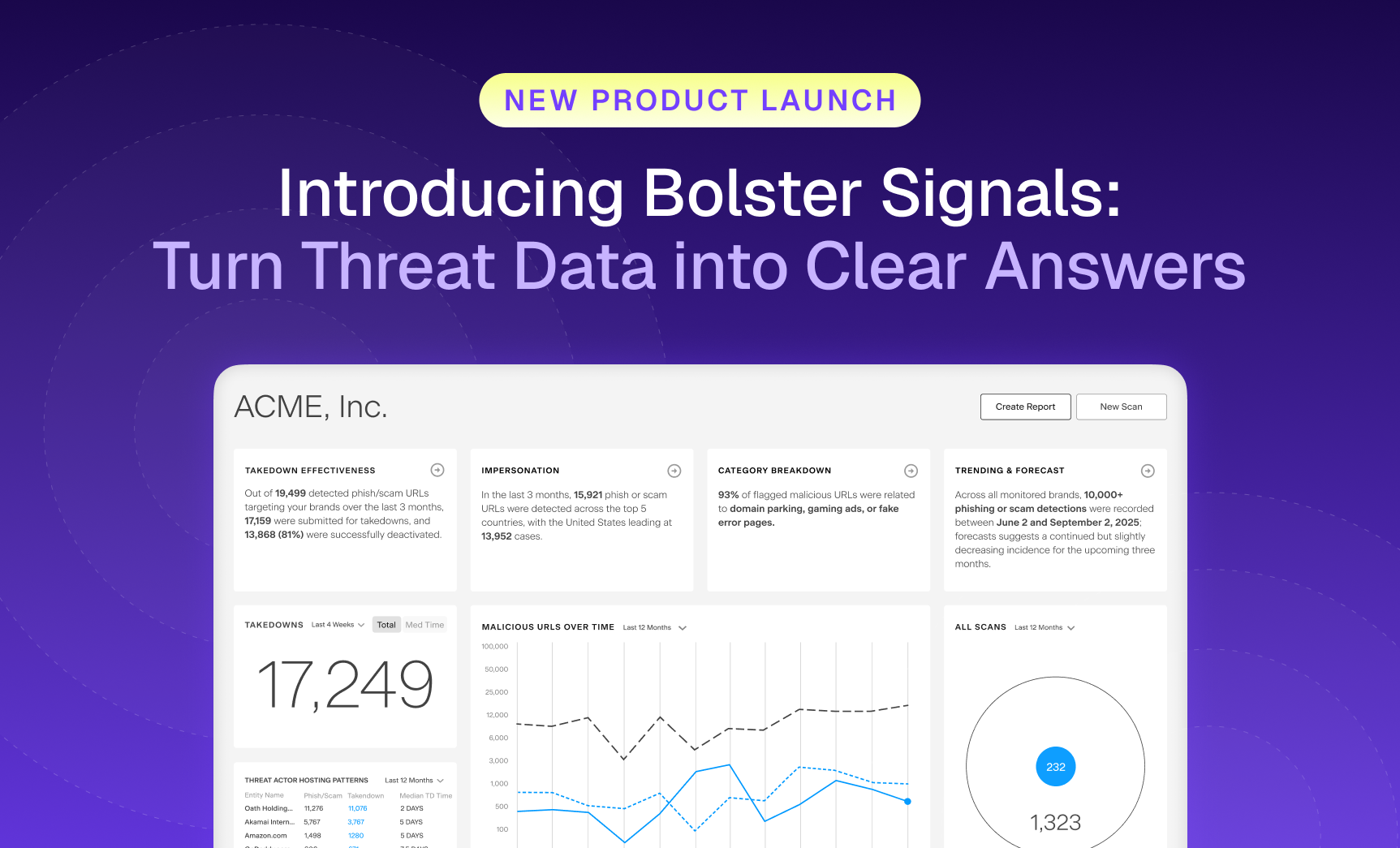
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
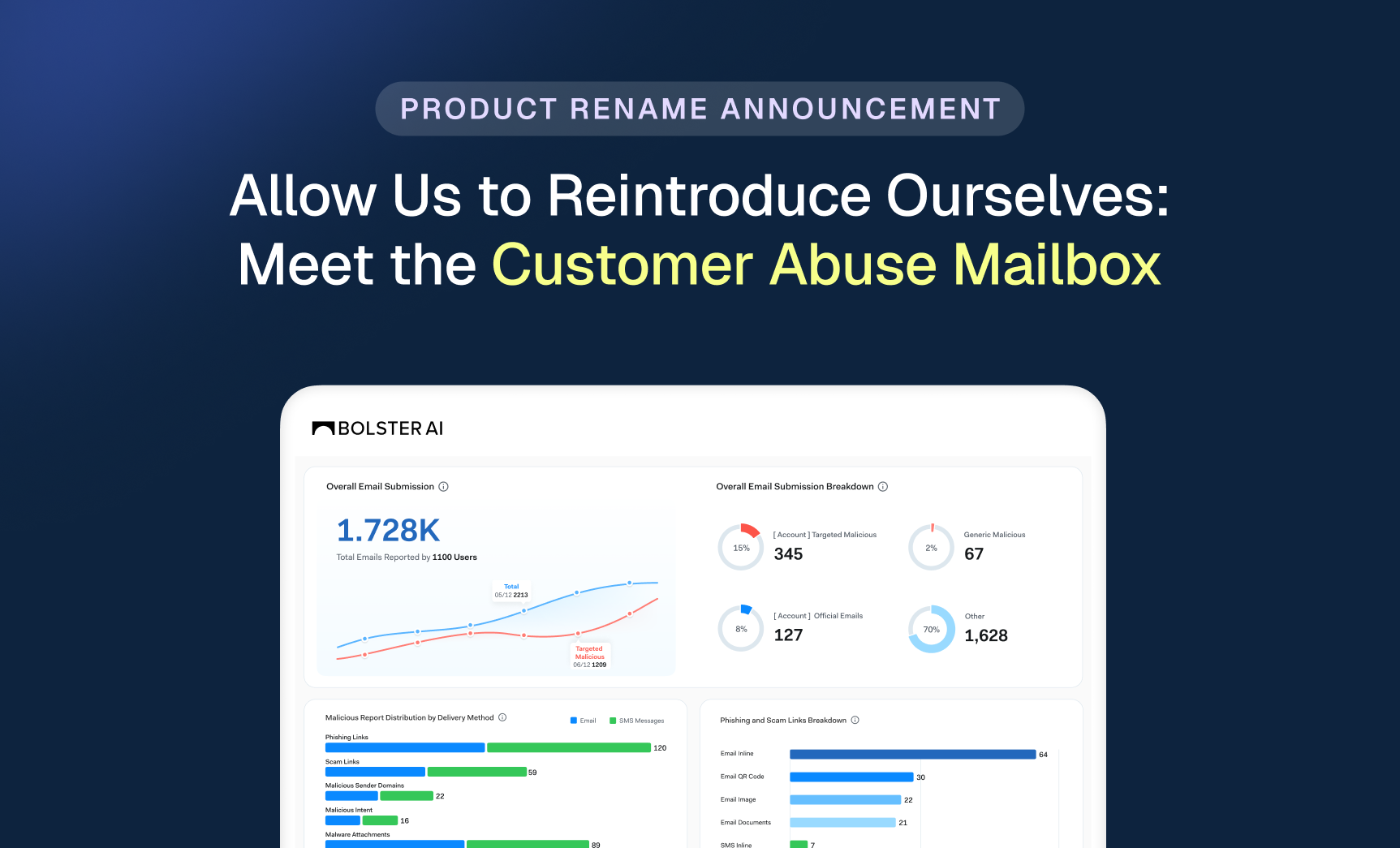
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
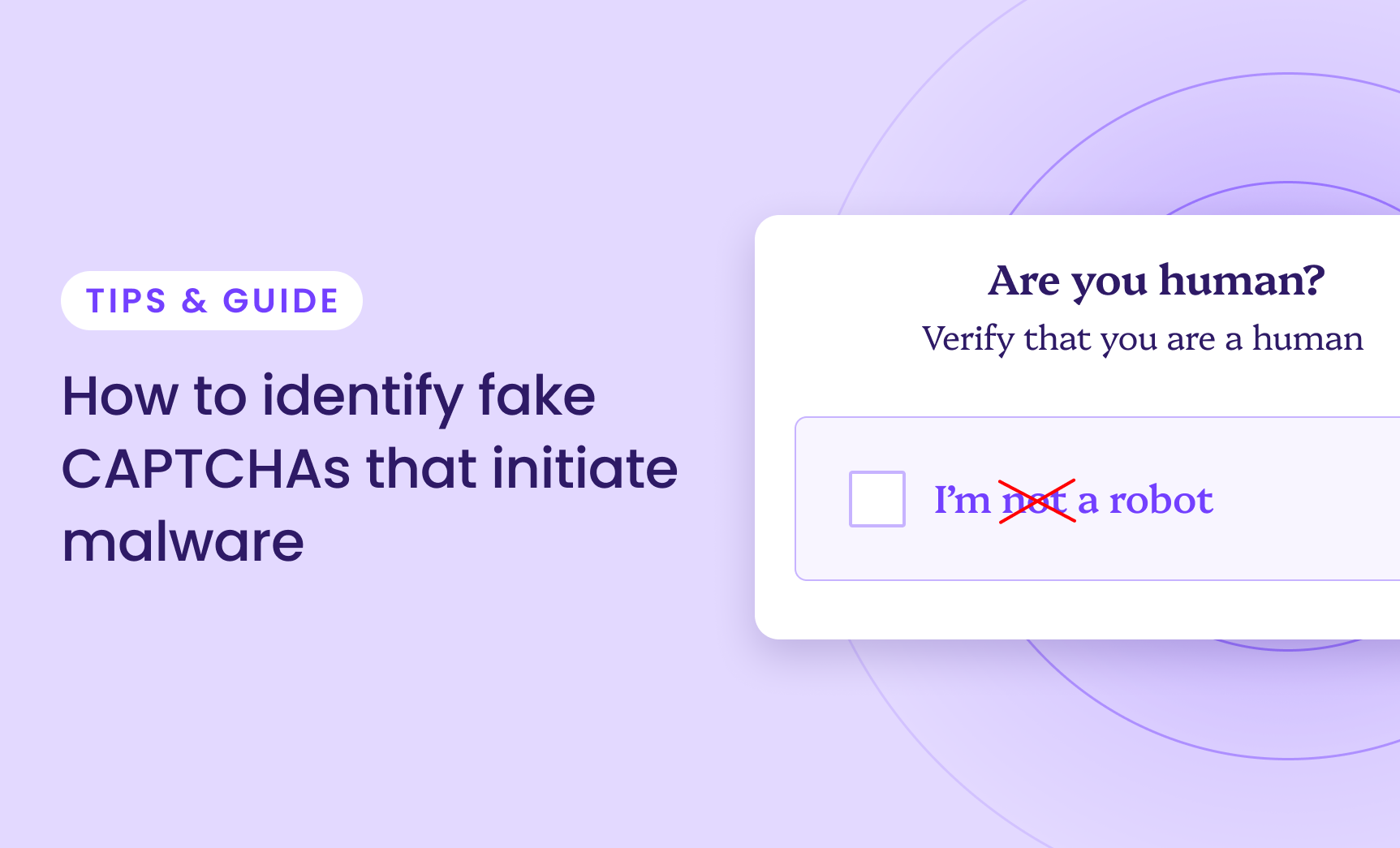
How to Avoid Fake CAPTCHA Scams That Initiate Malware
Online security measures like CAPTCHAs (Completely Automated Public Turing test…
AI Investment Fraud: How Scammers Set Traps
Whether it’s in stocks, real estate, bonds, or even cryptocurrency,…
ByBit Heist: Unraveling One of the Largest Crypto Thefts in History
ByBit Heist: Behind the Scenes The ByBit cryptocurrency exchange experienced…
DeepSeek Under Attack: How Scammers Are Using Fake Domains & Phishing to Target Users
Introduction: The Rise of DeepSeek & Emerging Threats DeepSeek has…
A Deep Dive into Business Email Compromise (BEC) Scams
Introduction Business Email Compromise (BEC) represents one of the most…
Postmarked by Fraud: Dissecting the Emirates Post Phishing Kit
“In the digital realm, not everything that glitters is gold.”…
WEB LLM Attacks: How AI is Being Weaponized on the Web
In the AI era, Large language models (LLMs) are increasingly…
Dark Web Phishing Attacks by Leveraging New Web Tools & AI
“An ounce of prevention is worth a pound of cure”…
The Click That Stole Holidays: Black Friday and Cyber Monday Scams Unmasked
The onset of Cyber Monday and Black Friday deals is…
Exploring the Risks of IPFS in Phishing Attacks
The InterPlanetary File System (IPFS) is a cutting-edge technology designed…
AI Fraud Detection in Finance: How Banks Use AI to Fight Money Laundering & More
The finance industry is in a race against increasingly sophisticated…
Cracking the Shield: Methods Hackers Use to Bypass MFA
Despite its apparent strength, Multi-Factor Authentication (MFA) is not immune…