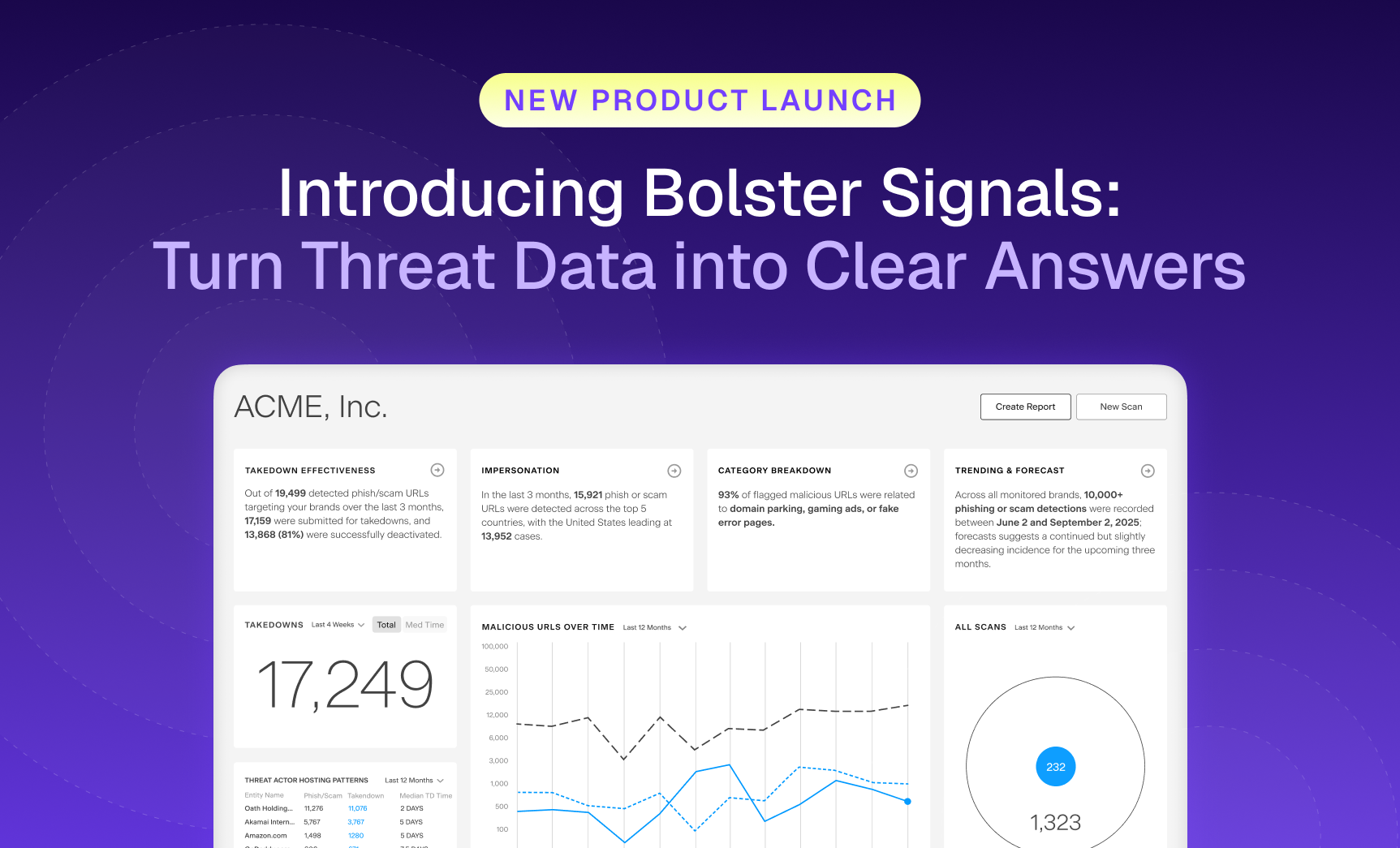
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
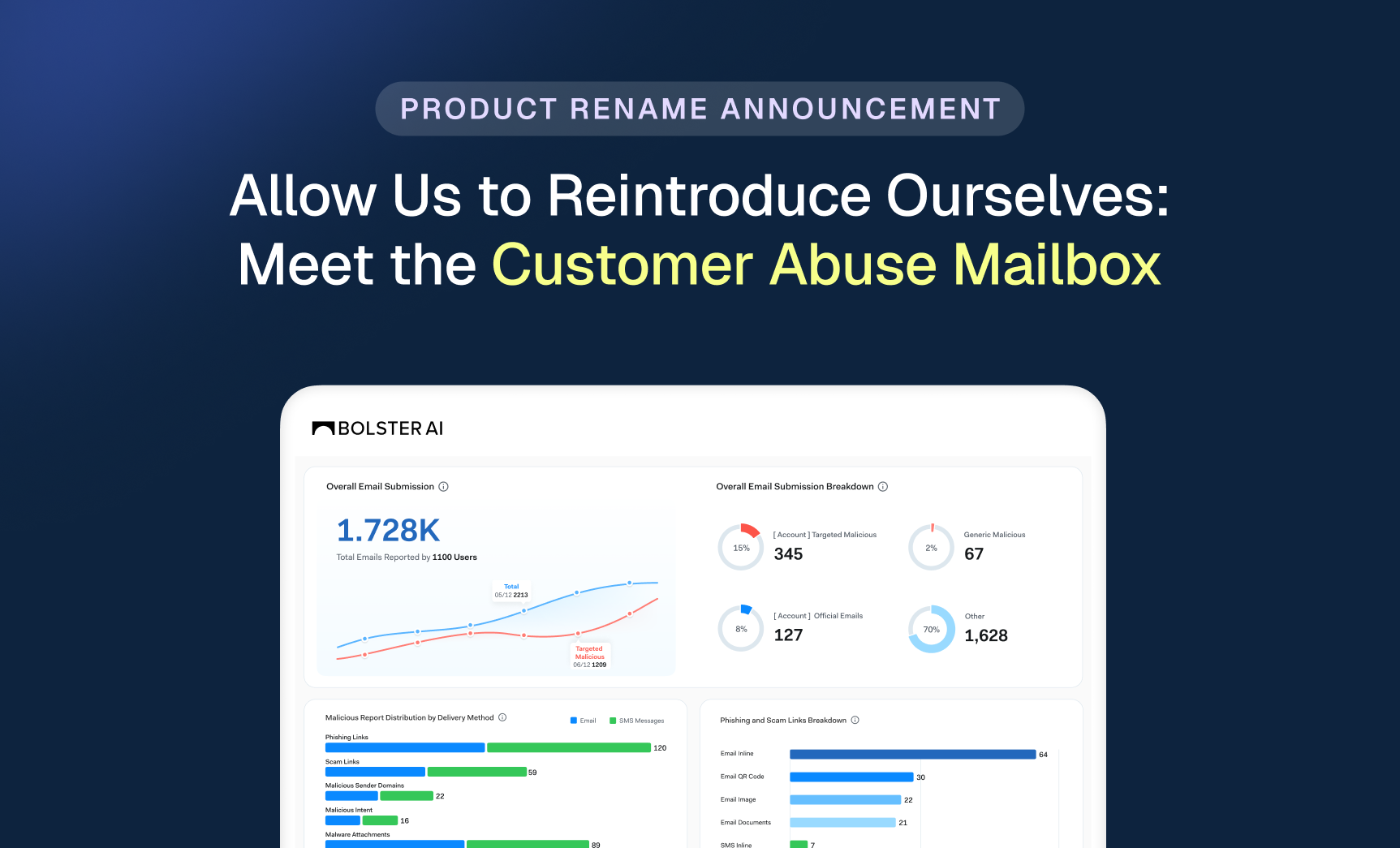
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Crypto Deceit: Fending Off The Phishing Nets Targeting Digital Assets
The growing allure of cryptocurrencies draws both investors and cybercriminals…
From FOMO to Fraud: Understanding Crypto Scams in Market Booms
Fear of Missing Out in the cryptocurrency world can lead…
Navigating Tax Season Safely: Understanding the Threat of IRS Scams and Phishing Operations
The sophistication of IRS scams and phishing attempts targeting taxpayers…
Quishing: The Rising Threat & Dangers of QR Code Phishing
QR codes have transitioned from a symbol of convenience to…
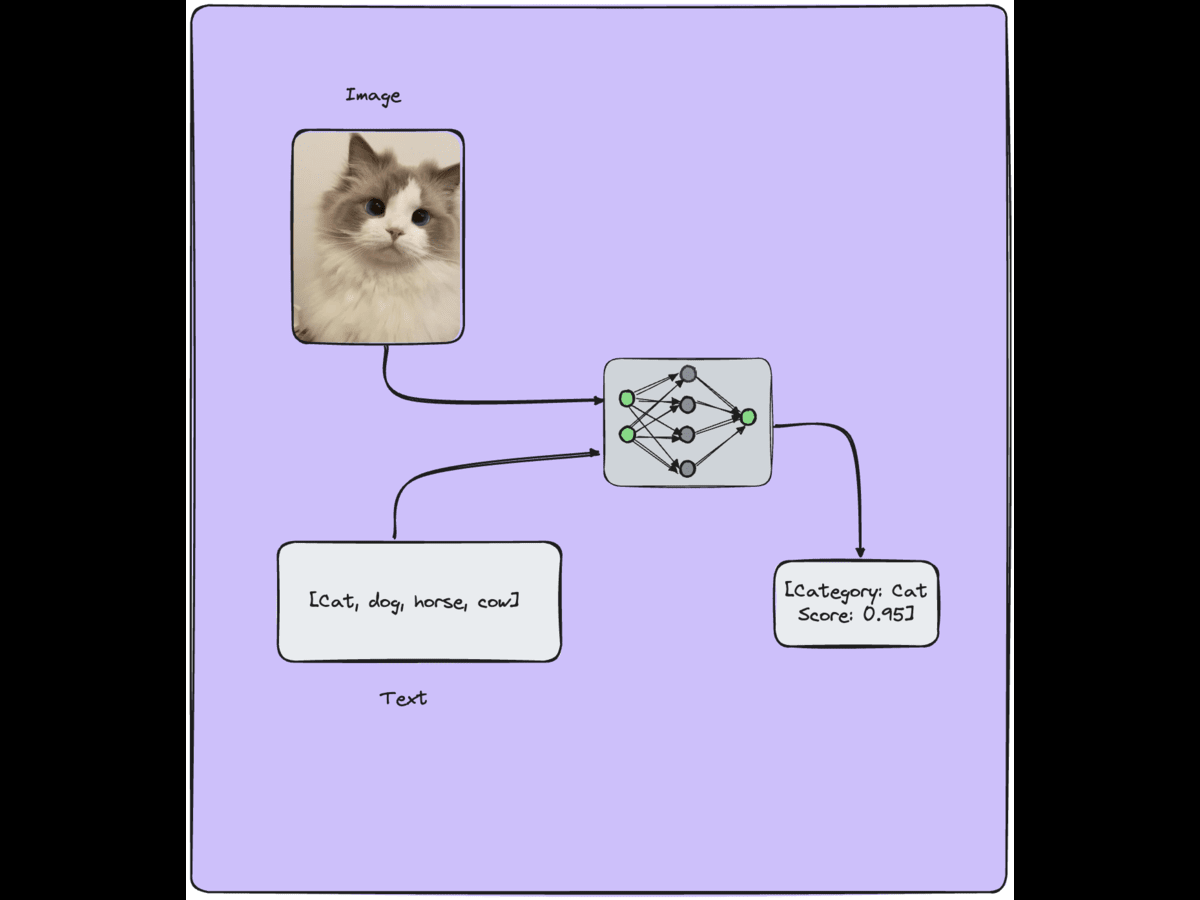
Vision Language Models Applications & Learning Strategies
Vision Language Models (VLMs) have applications in various fields, including…
Telegram Phishing Bot Token Being Stolen from Scammers
At Bolster Research Labs, we recently observed that phishing kit…
Ad-ventures: Investigating the Misuse of Google Ads in Malvertising Campaigns
In the sprawling extent of the internet, Google Ads has…
Stealer Logs & The Threat That is Compromising Security
The arms race between cyber defenders and attackers is becoming…
Image Similarity for Brand Detection: A Comparison Between BEiT, SWIN and ViT-MAE
Image similarity has emerged as one of the most powerful…
Identifying Compromised Antivirus Software & Fake Sites
Antivirus vendors have significantly been impacted by the latest phishing…
Dissecting the Phishing Kit behind the Axis Bank Reward Points Campaign
Phishing campaigns targeting banking and financial institutions have always been…
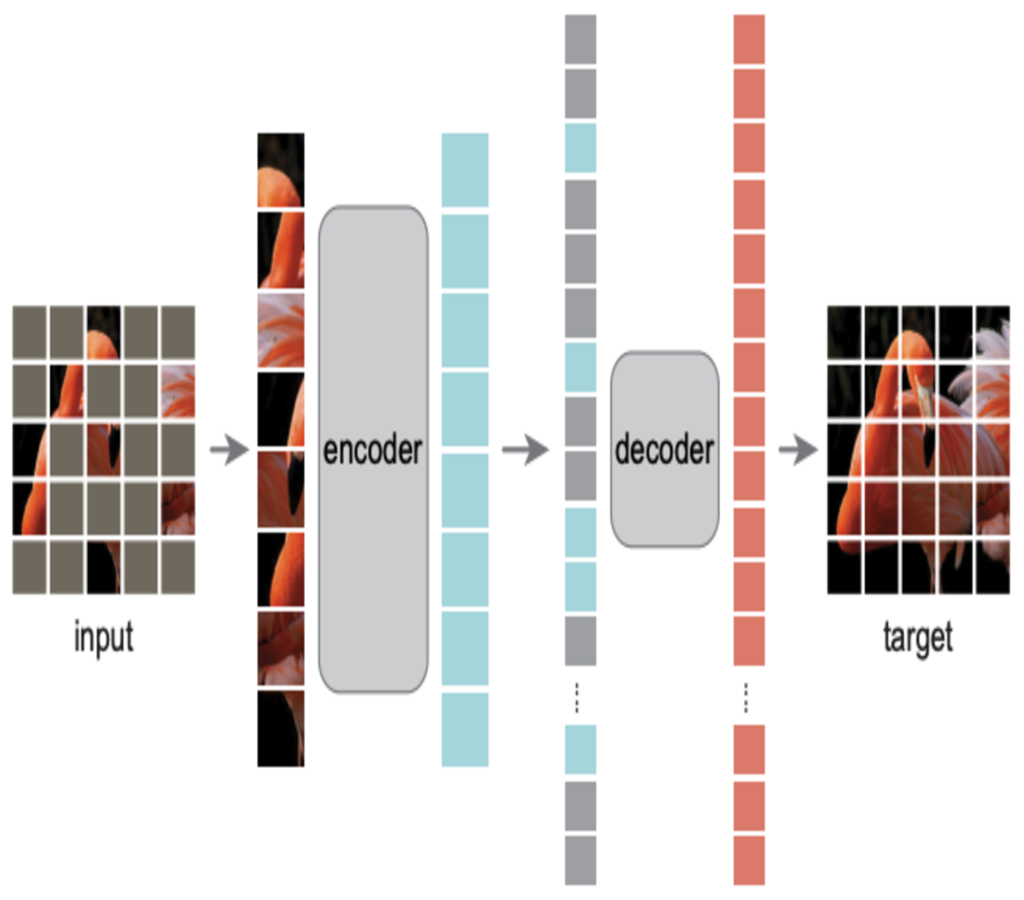
What is VIT-MAE? Scalable Learning for Vision Transformers.
Unprecedented gains in hardware capabilities and model sizes have compelled…