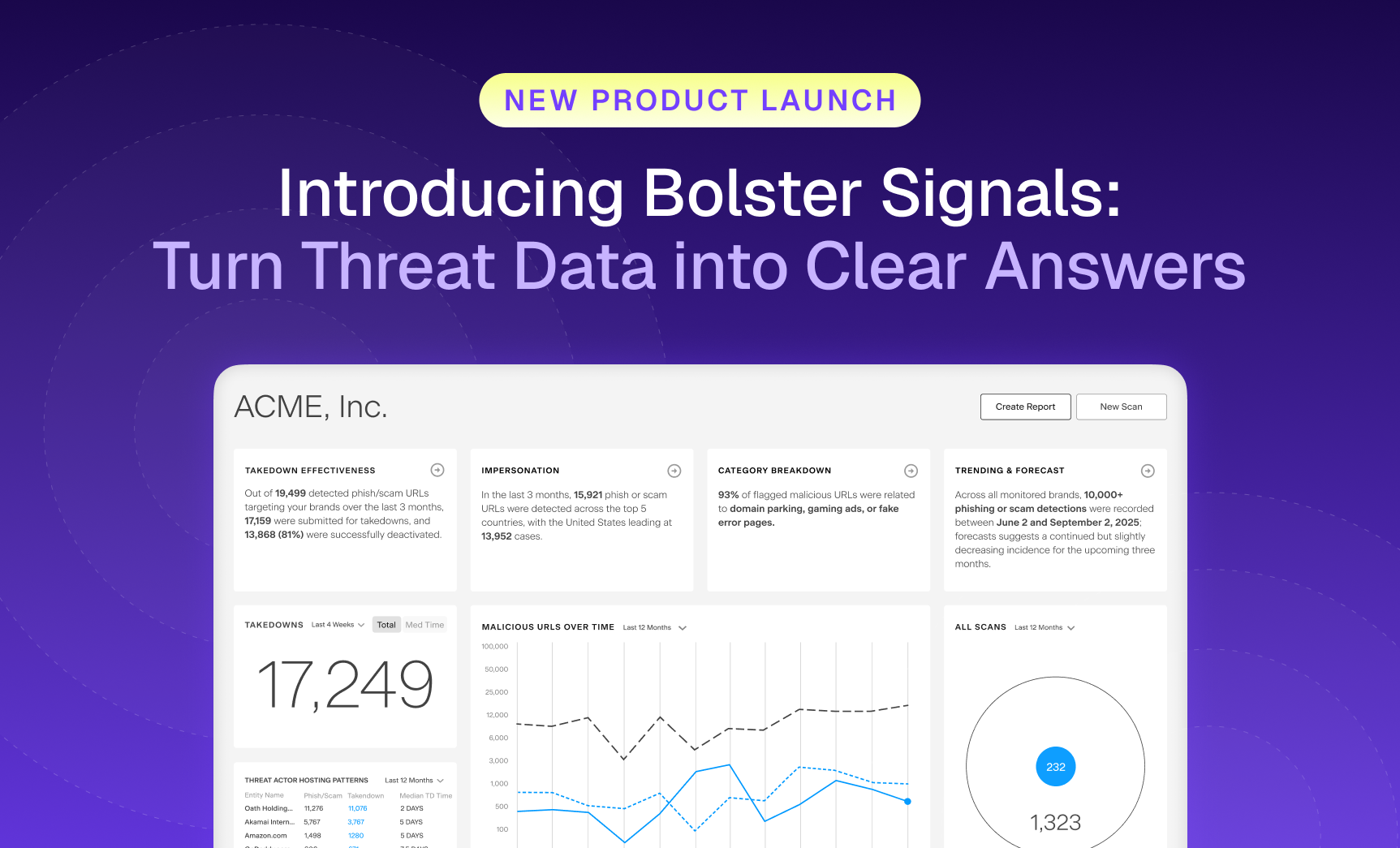
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
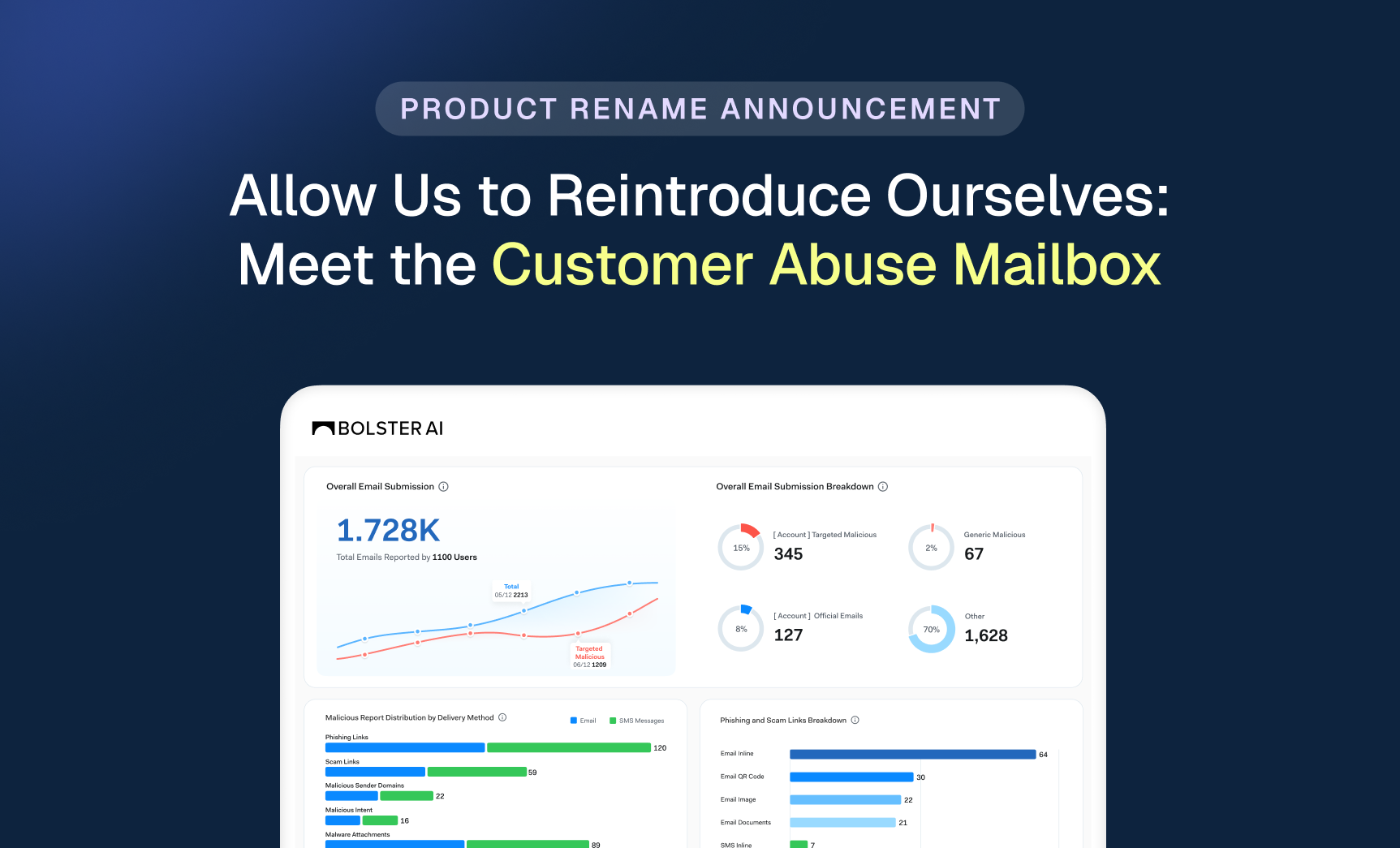
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
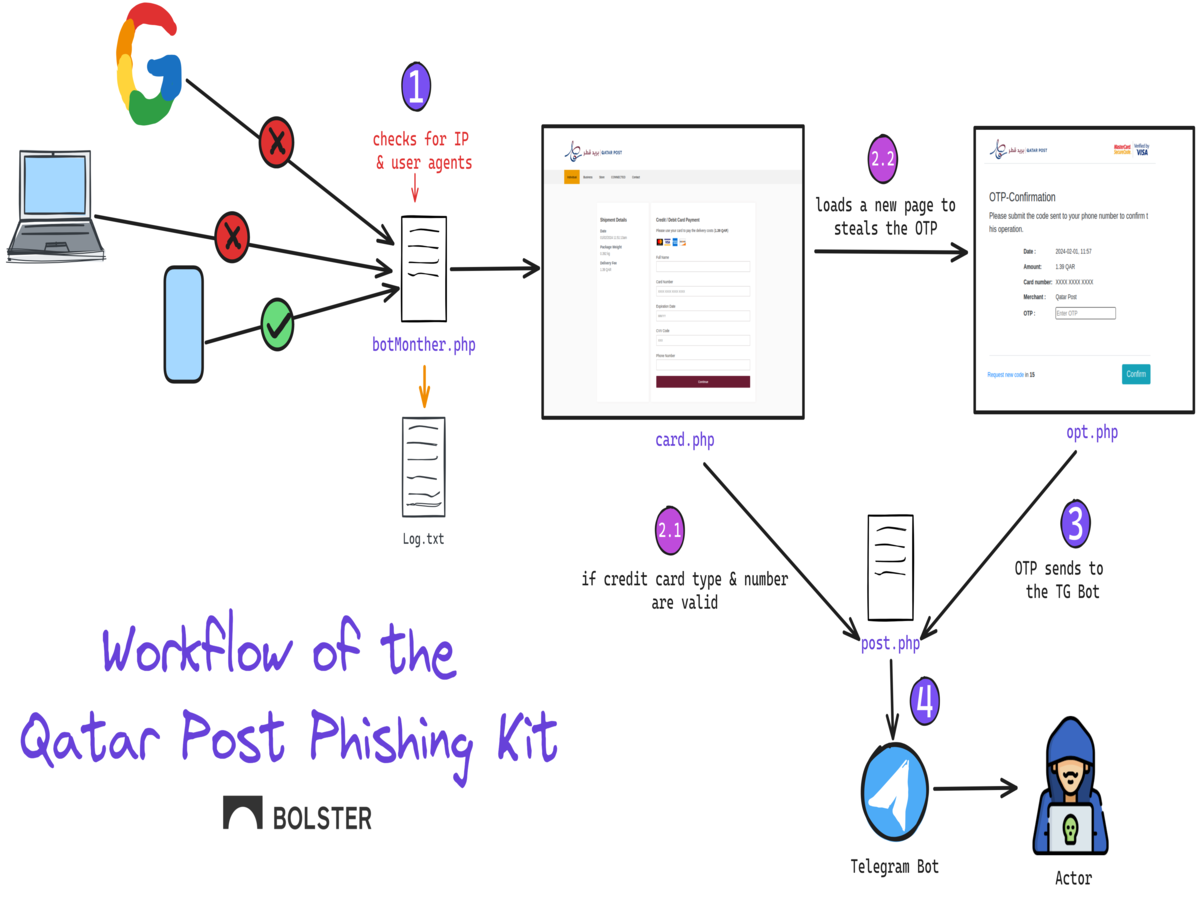
Dissecting the Newest Phishing Kit Targeting the Qatar Post
Name brand postal services have been increasingly targeted by phishing…
The Dark Underbelly of the Internet: Bulletproof Hosting and Phishing Epidemic
What is Bullet Proof Hosting [BPH]? Within the digital community,…
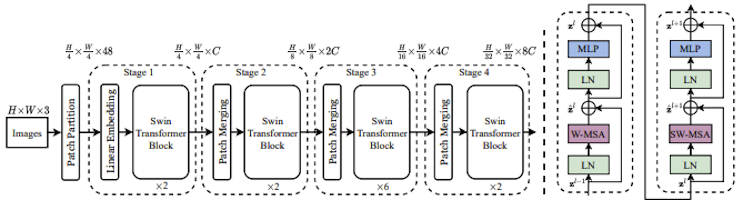
SWIN Transformers Explained: The Best of Two Worlds
A Swin Transformer is a vision transformer architecture that processes…
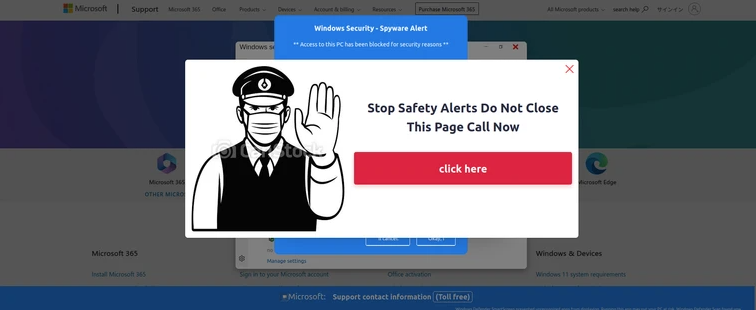
Analyzing Advanced Multi-Lingual Tech Support Phishing Kits Hosted on SaaS Providers
The Tech Support Scam consistently remains in the spotlight due…
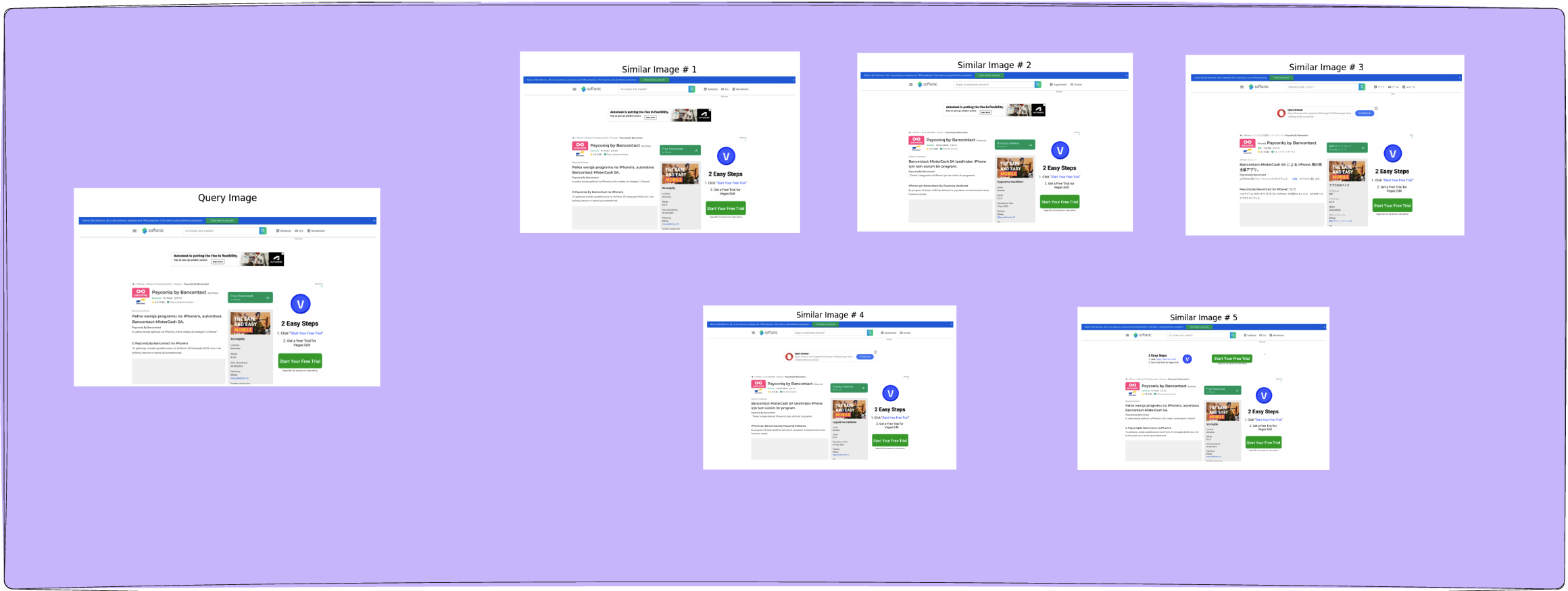
Beyond Hashing: The Future of Anti-Phishing is Image Similarity Search
Computer vision modules are a critical component in a cybersecurity…
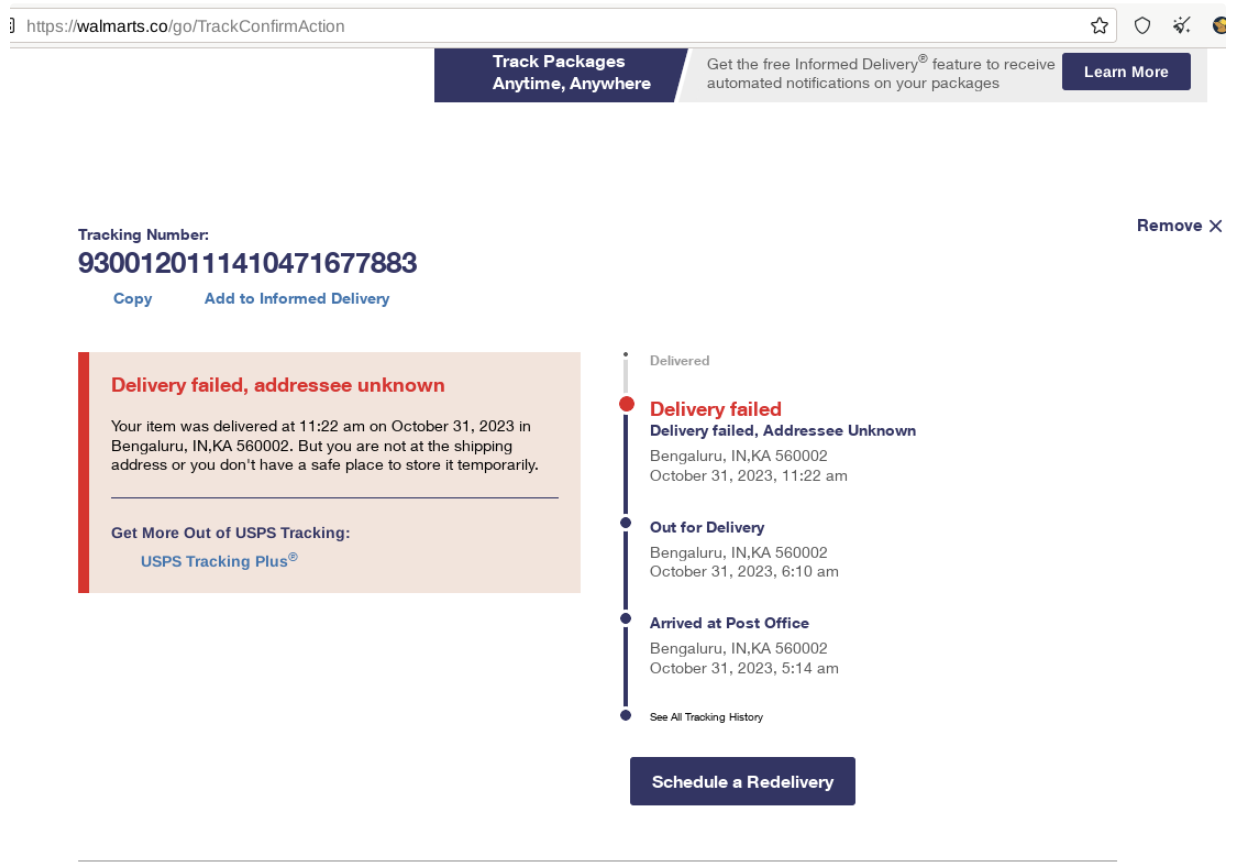
Vast USPS Delivery Phishing Campaign Sees Threat Actors Abusing Freemium Dynamic DNS and SaaS Providers
You may be familiar with the common phishing tactics like…
ICC World Cup 2023: Unmasking the Scams and Threats Targeting Fans Worldwide
The ICC World Cup 2023, the 13th edition of…
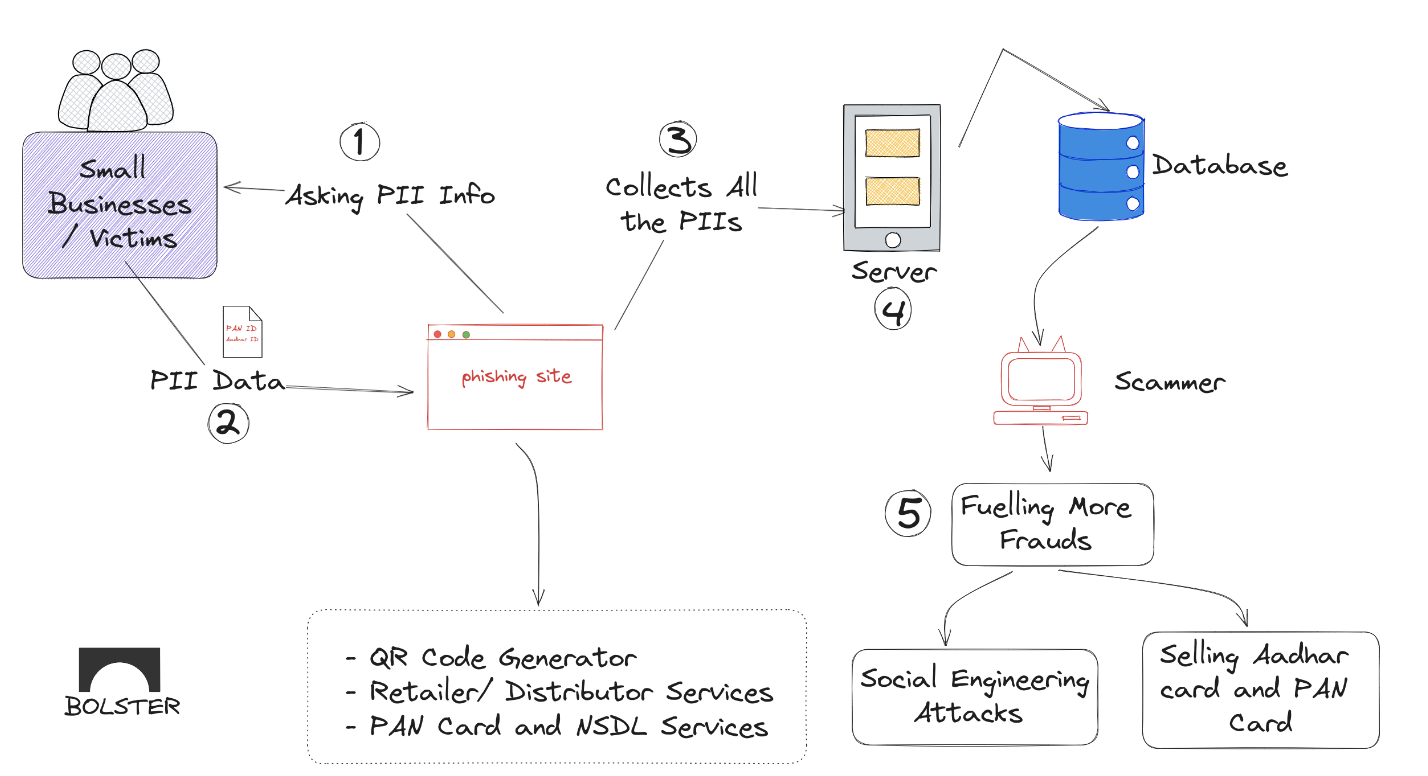
Under the Radar: Phishing Websites Masquerading as UPI Gateways to Secretly Steal Customer Data
Many threat actors are moving away from utilizing brand…
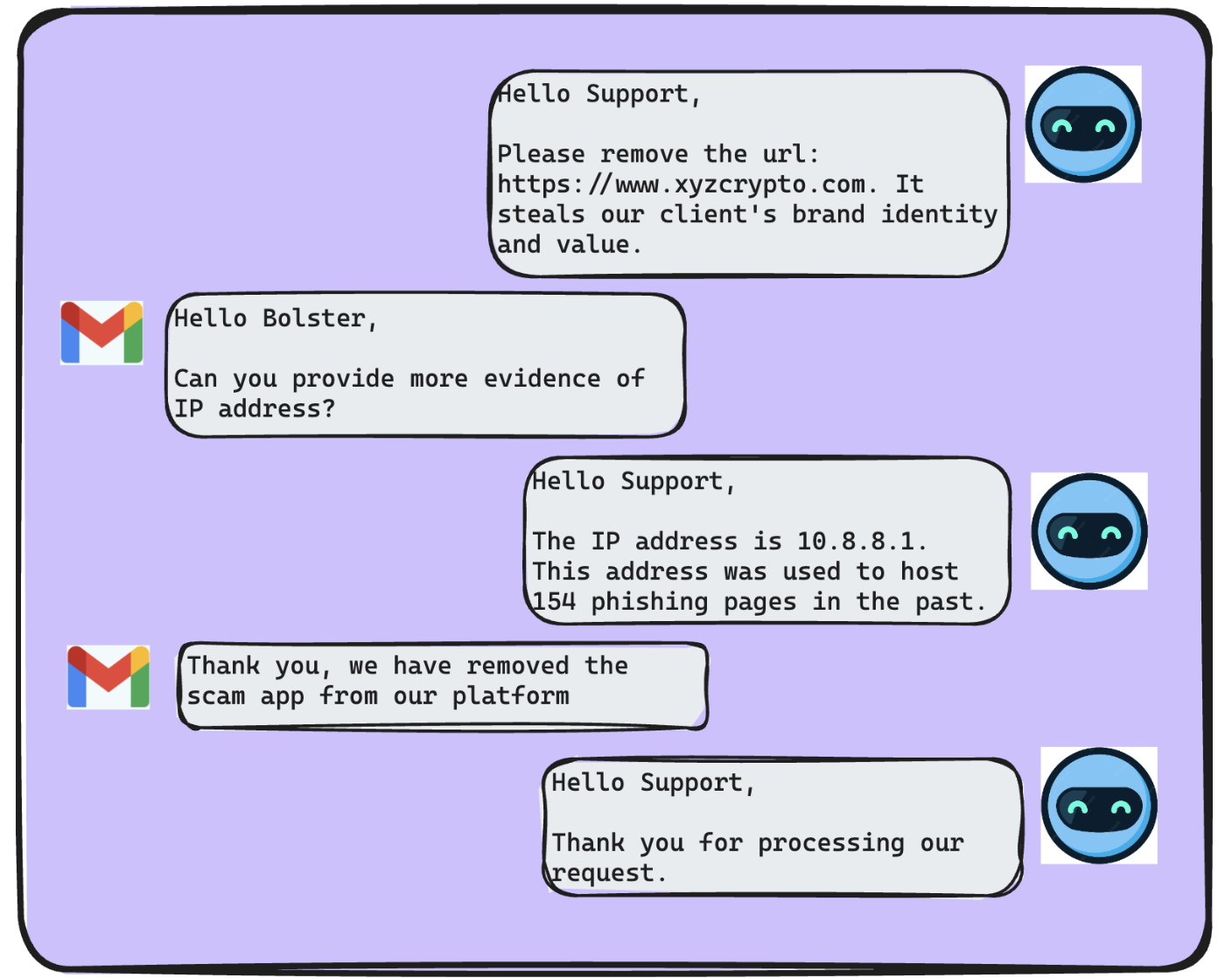
Automating Multi-Touch Takedowns with Large Language Models at Scale
As part of our Large Language Models at work…
Empowering Brand Protection: Large Language Models and Their Role in Webpage Intent Identification for Brand Safety
Pattern recognition is a key skill that has enabled…
Evaluating Web Scraping, Crawling, and Automation with NodeJS Libraries
This blog is part 1 of a web scraping…
How Decentralized Web Hosting is Used in Phishing Campaigns
Decentralized web hosting moves away from reliance on centralized…