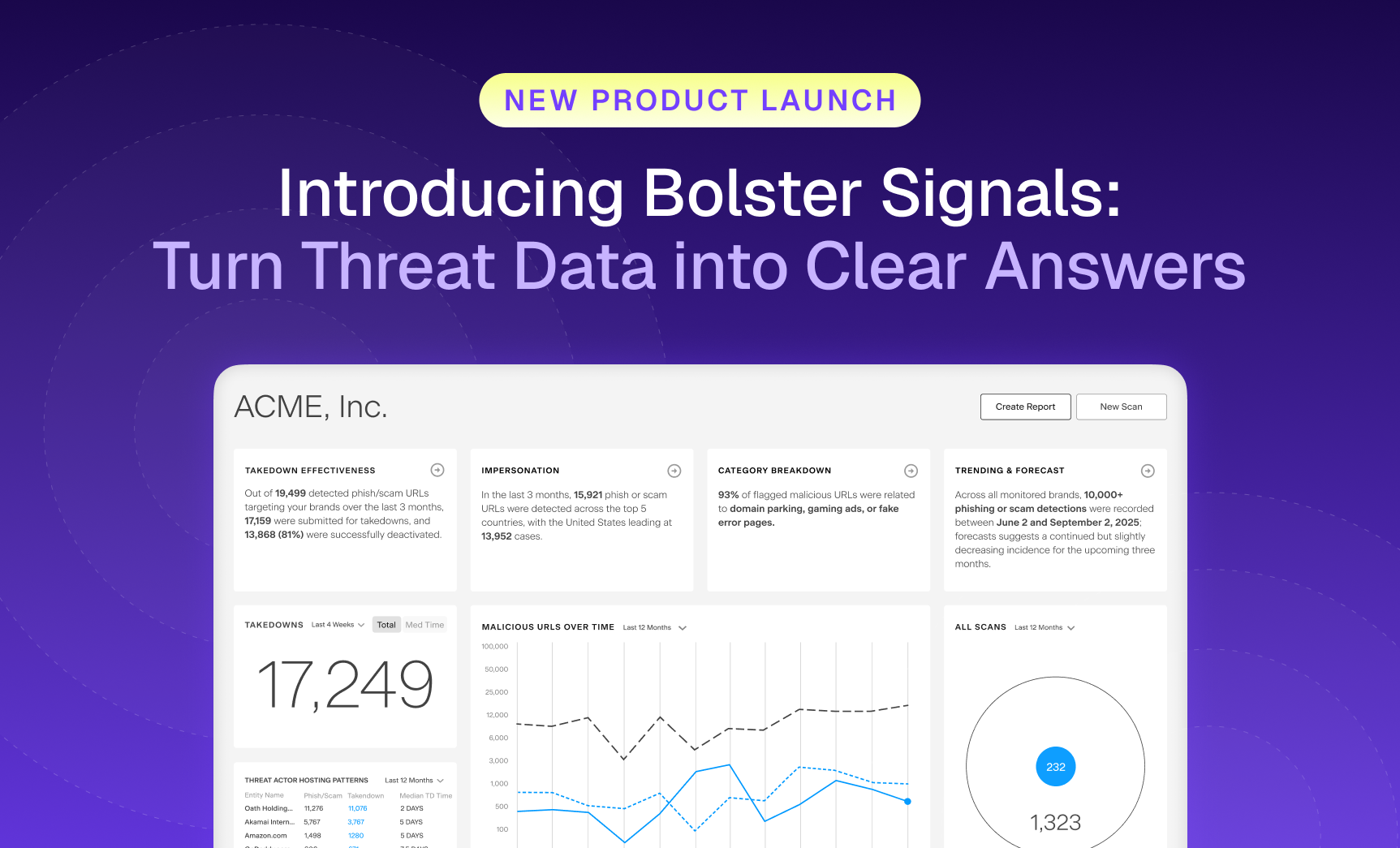
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
How to Do a Dark Web Scan: The Complete Playbook
Your organization’s credentials are probably already on the dark web; you just don’t know it yet. With 5.5 billion records exposed in 2024 and breaches.
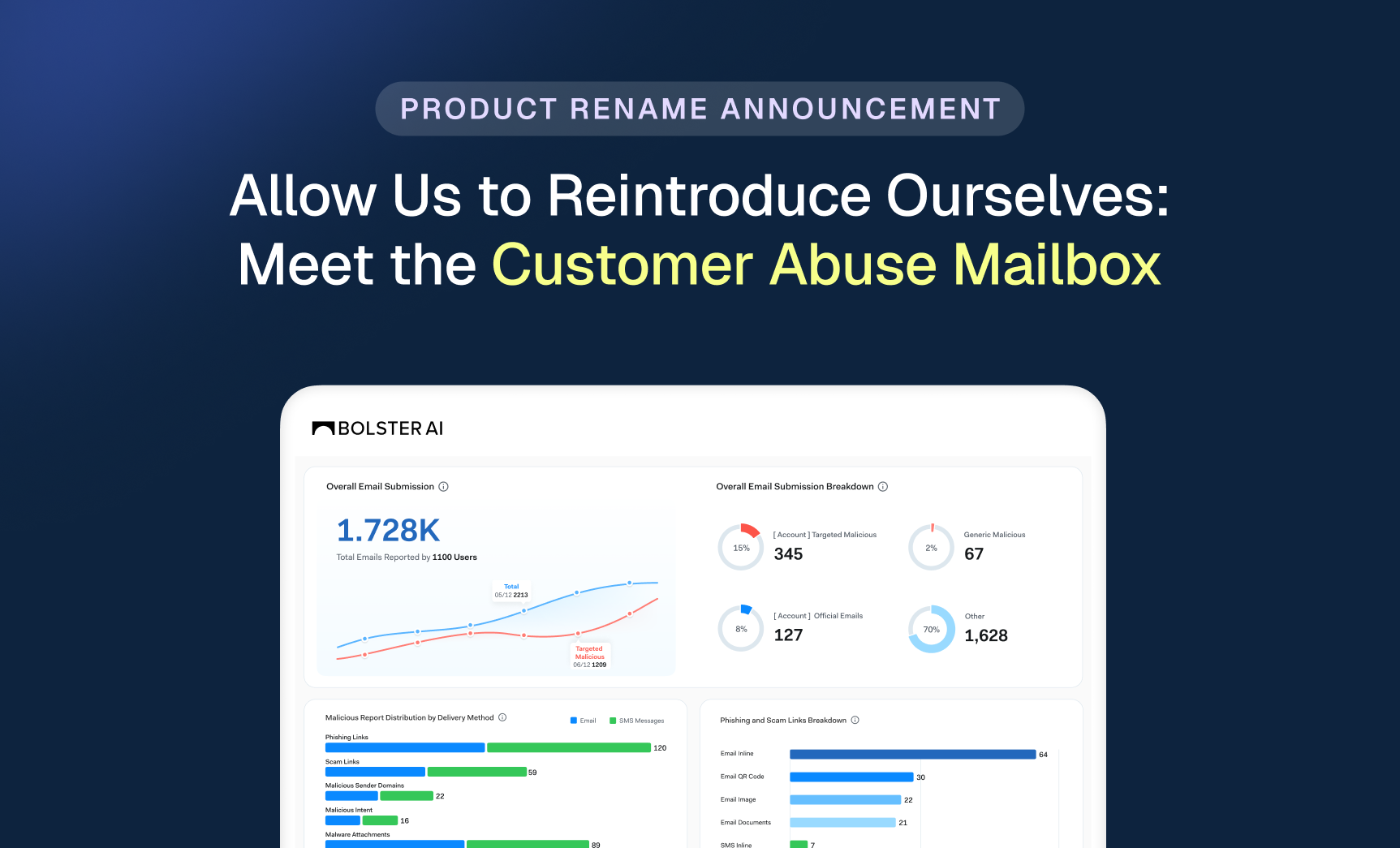
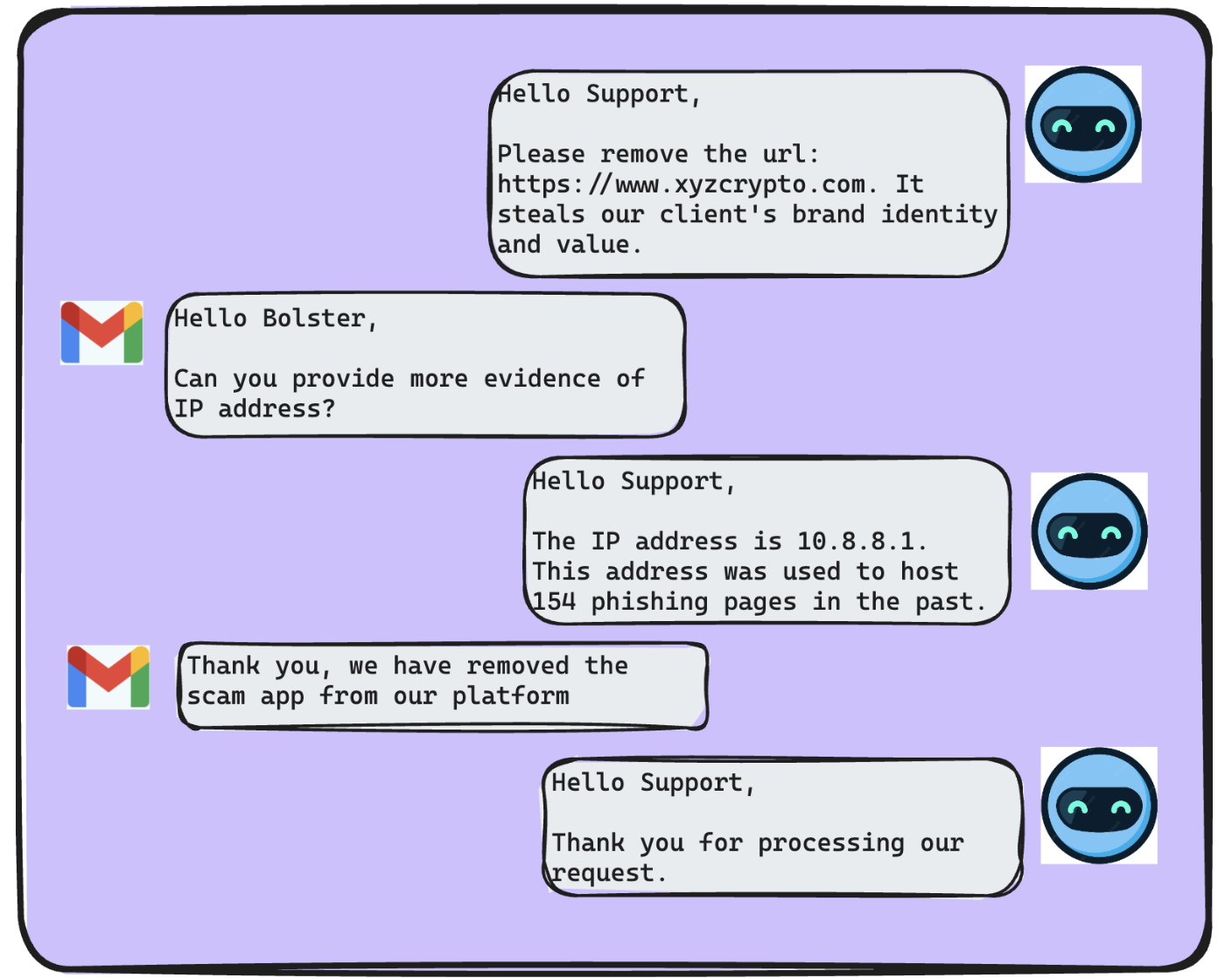
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
A Pocket Guide to Multi-Channel Phishing Defense
Imagine this scenario, highlighting the need for multi-channel phishing defense: …
Online Shopping Tips to Protect Yourself During Black Friday 2023
As the holiday season swings into full gear, shoppers…
Using LLM's for Heightened Cybersecurity: Supercharging Automated Takedowns With GPT
It takes a lot to surprise engineers working on…
Brand Impersonation Attacks: Which Industries are Most at Risk?
In late 2022, American Express was at the center…
ICC World Cup 2023: Unmasking the Scams and Threats Targeting Fans Worldwide
The ICC World Cup 2023, the 13th edition of…
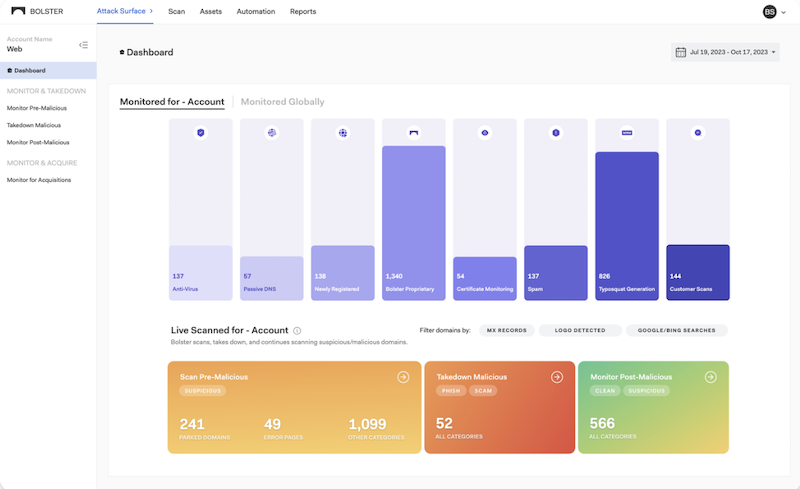
A Visual Journey: Exploring the Redesigned Bolster Dashboard
One of the top challenges that security practitioners often…
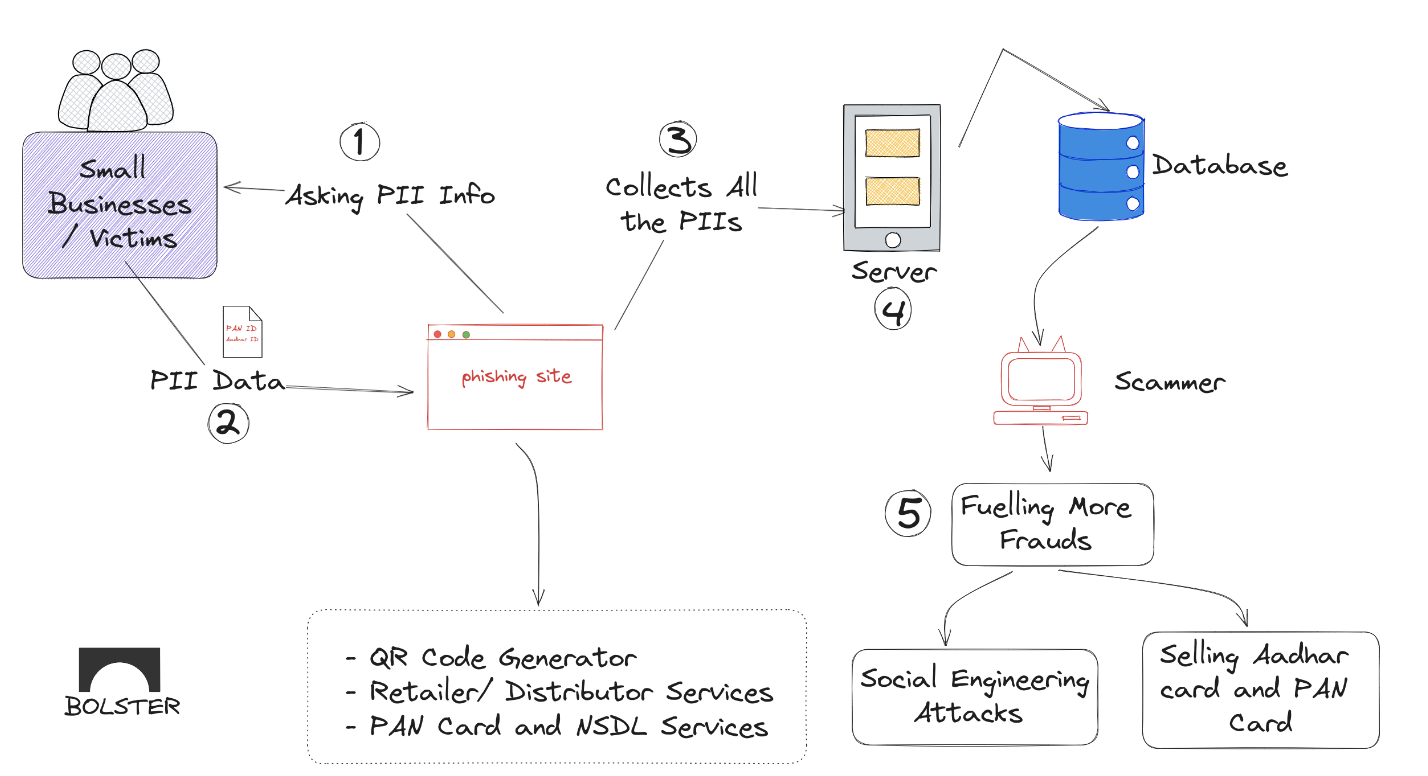
Under the Radar: Phishing Websites Masquerading as UPI Gateways to Secretly Steal Customer Data
Many threat actors are moving away from utilizing brand…
Automating Multi-Touch Takedowns with Large Language Models at Scale
As part of our Large Language Models at work…
5 Strategies for Reliable Protection Against BEC Scams
The recent Cloudflare 2023 Phishing Threats Report unravels many…
Empowering Brand Protection: Large Language Models and Their Role in Webpage Intent Identification for Brand Safety
Pattern recognition is a key skill that has enabled…
4 Key Trends from the Cloudflare 2023 Phishing Threats Report
In 2023, email remains one of the most popular…
What is Trap Phishing? 9 Ways Your Business Can Be Impacted.
Trap phishing is a type of targeted phishing attack that…