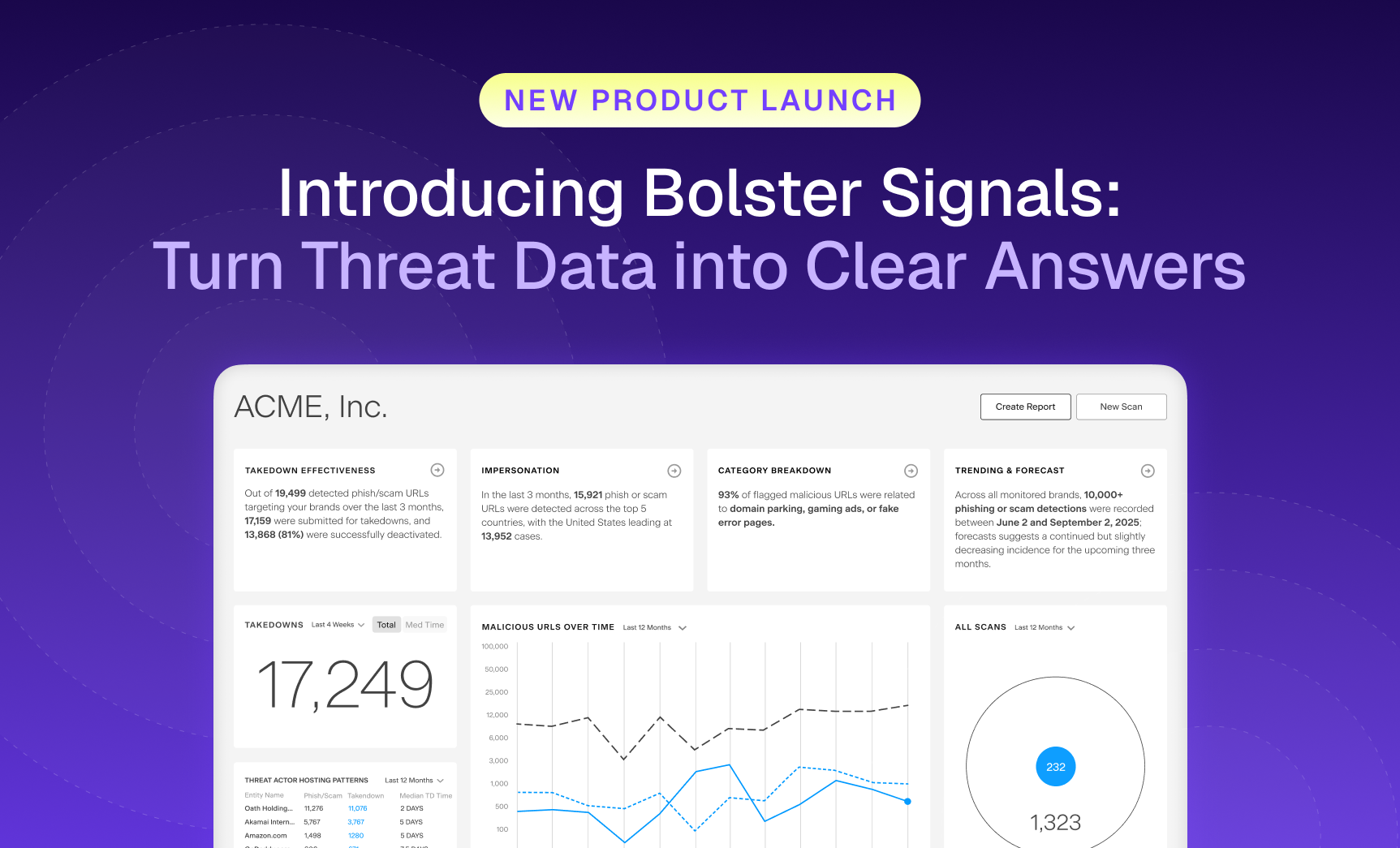
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
How to Do a Dark Web Scan: The Complete Playbook
Your organization’s credentials are probably already on the dark web; you just don’t know it yet. With 5.5 billion records exposed in 2024 and breaches.
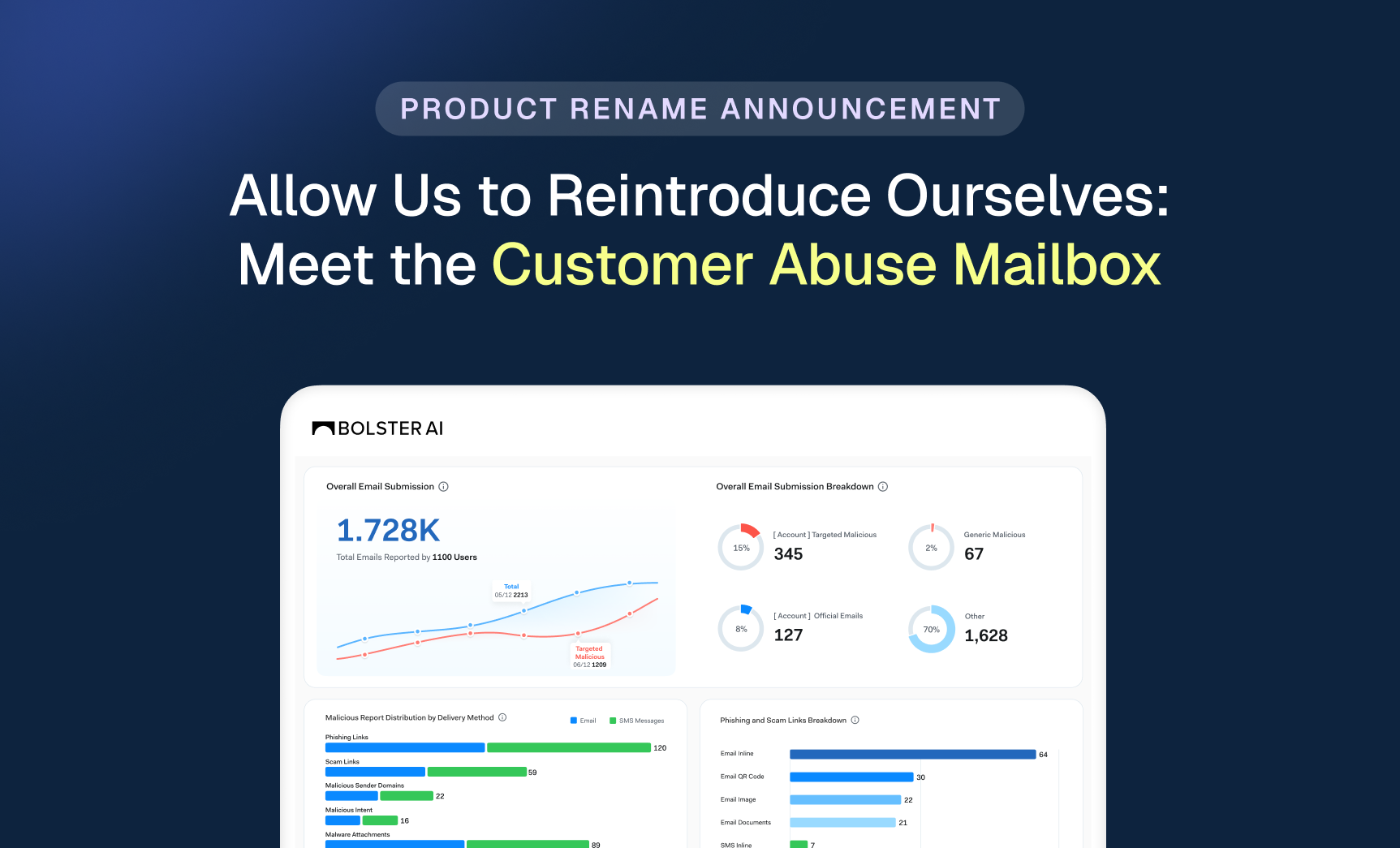
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Identifying Compromised Antivirus Software & Fake Sites
Antivirus vendors have significantly been impacted by the latest phishing…
Dissecting the Phishing Kit behind the Axis Bank Reward Points Campaign
Phishing campaigns targeting banking and financial institutions have always been…
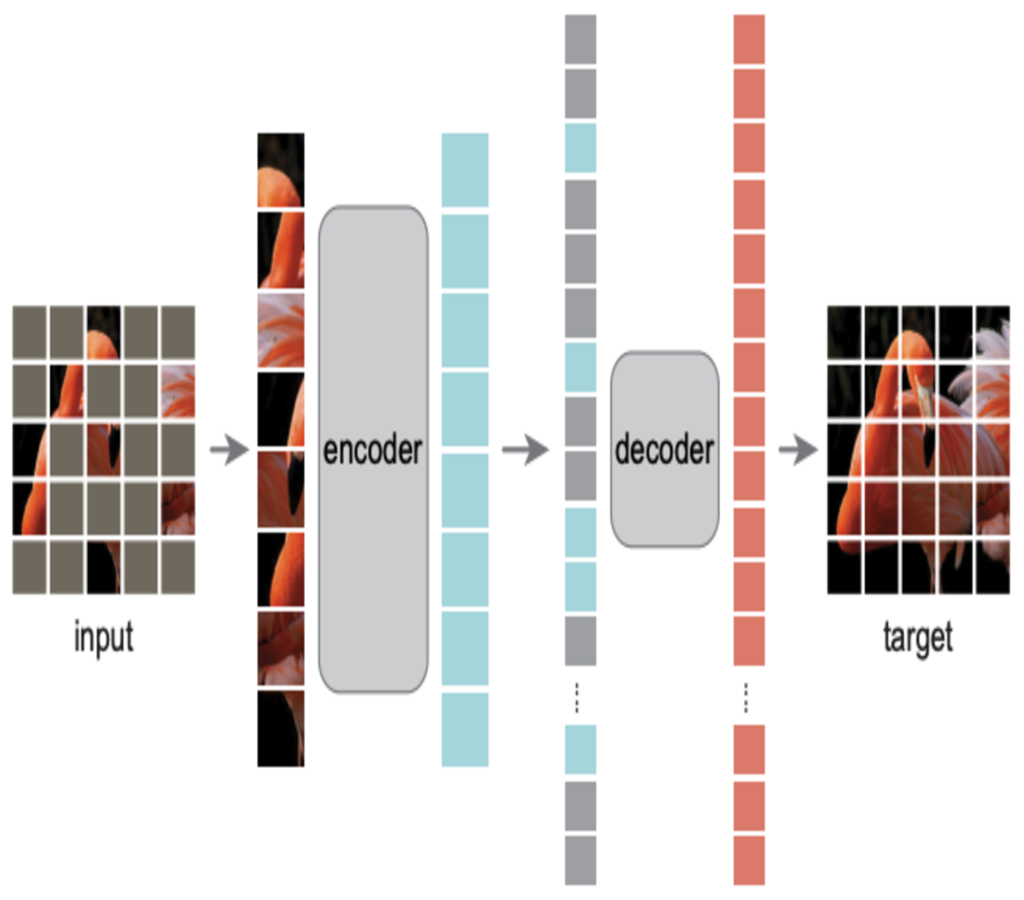
What is VIT-MAE? Scalable Learning for Vision Transformers.
Unprecedented gains in hardware capabilities and model sizes have compelled…
A Global Crisis: What Companies Must Do to Avoid Legal Ramifications of Phishing Attacks
It wasn’t that long ago when phishing attacks were simply…
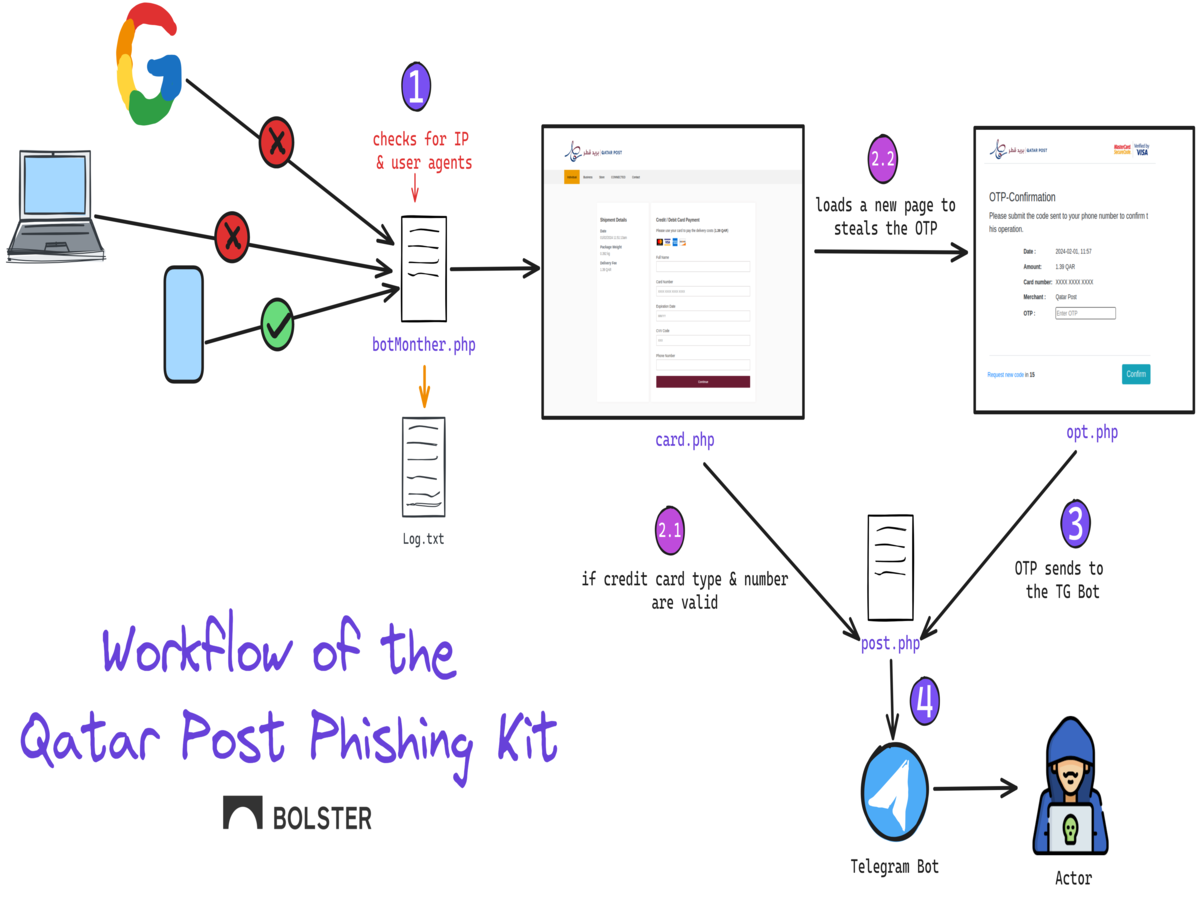
Dissecting the Newest Phishing Kit Targeting the Qatar Post
Name brand postal services have been increasingly targeted by phishing…
The Dark Underbelly of the Internet: Bulletproof Hosting and Phishing Epidemic
What is Bullet Proof Hosting [BPH]? Within the digital community,…
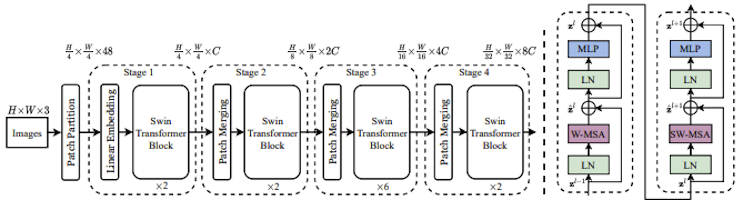
SWIN Transformers Explained: The Best of Two Worlds
A Swin Transformer is a vision transformer architecture that processes…
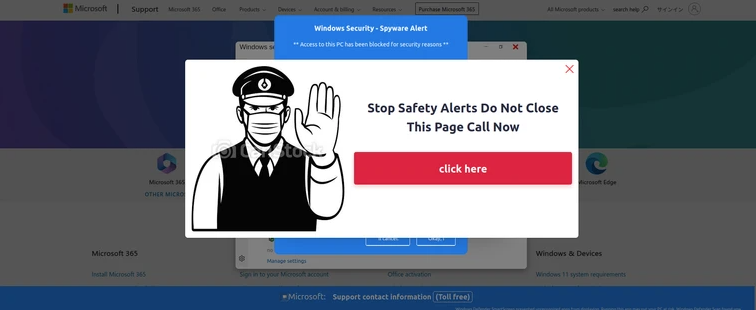
Analyzing Advanced Multi-Lingual Tech Support Phishing Kits Hosted on SaaS Providers
The Tech Support Scam consistently remains in the spotlight due…
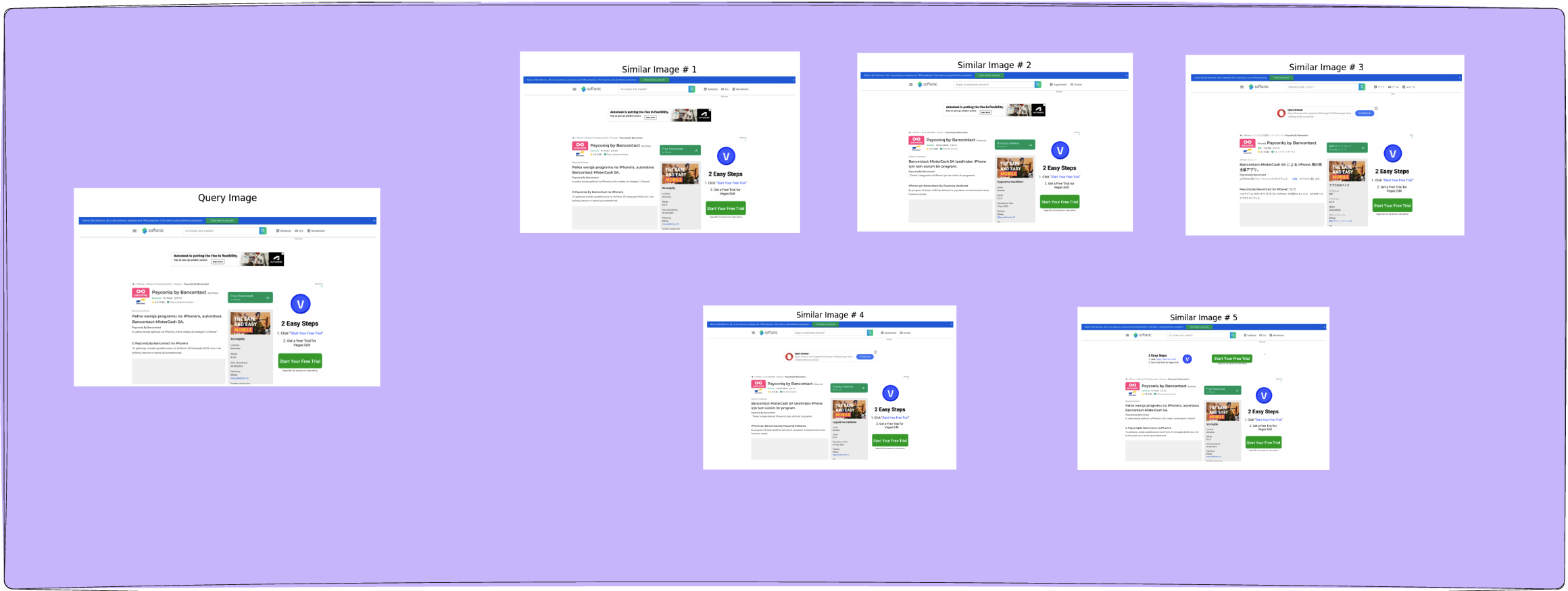
Beyond Hashing: The Future of Anti-Phishing is Image Similarity Search
Computer vision modules are a critical component in a cybersecurity…
The Year in Review: Top 10 Scam Trends From 2023
In today’s increasingly digital world, cyber scams have become a…
How to Avoid Falling for Gift Card Scams This Holiday Season
The holiday season is an exciting time of year, bringing…
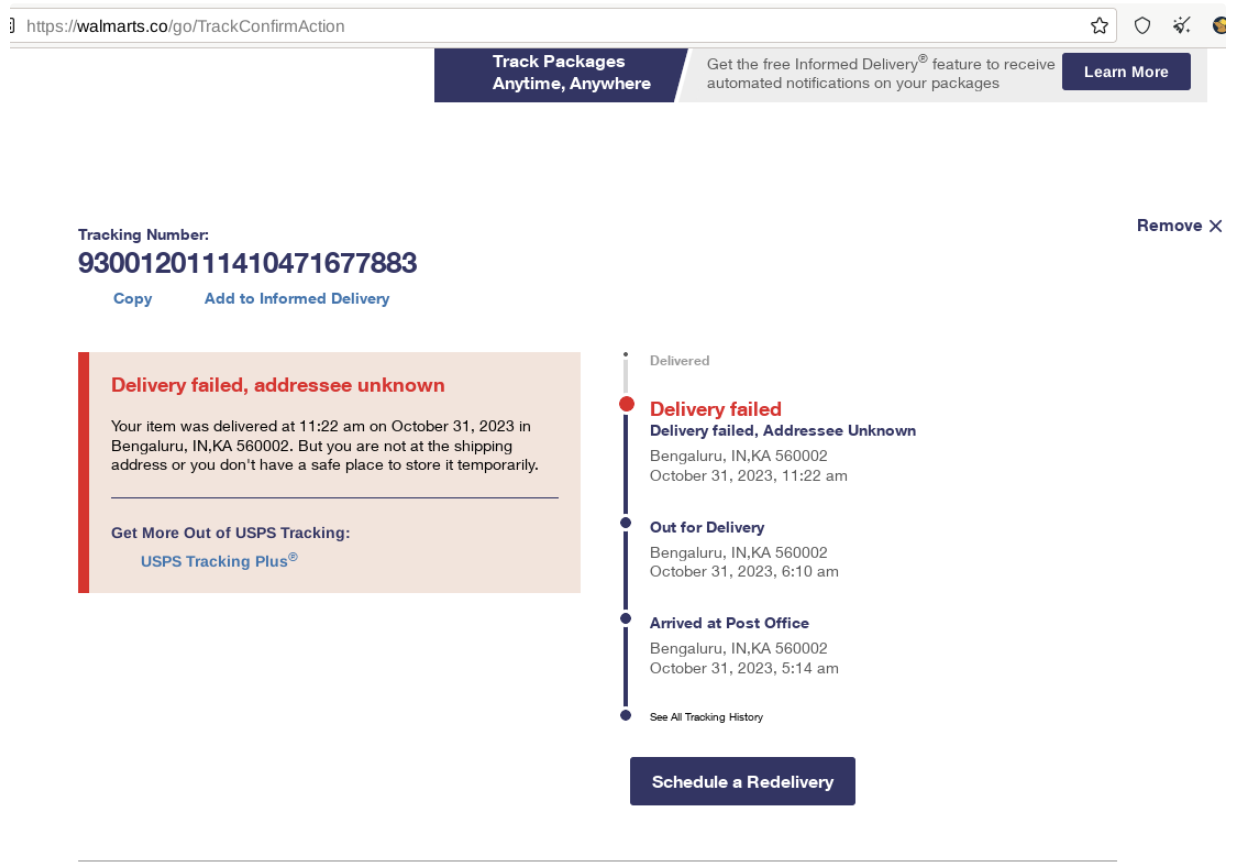
Vast USPS Delivery Phishing Campaign Sees Threat Actors Abusing Freemium Dynamic DNS and SaaS Providers
You may be familiar with the common phishing tactics like…