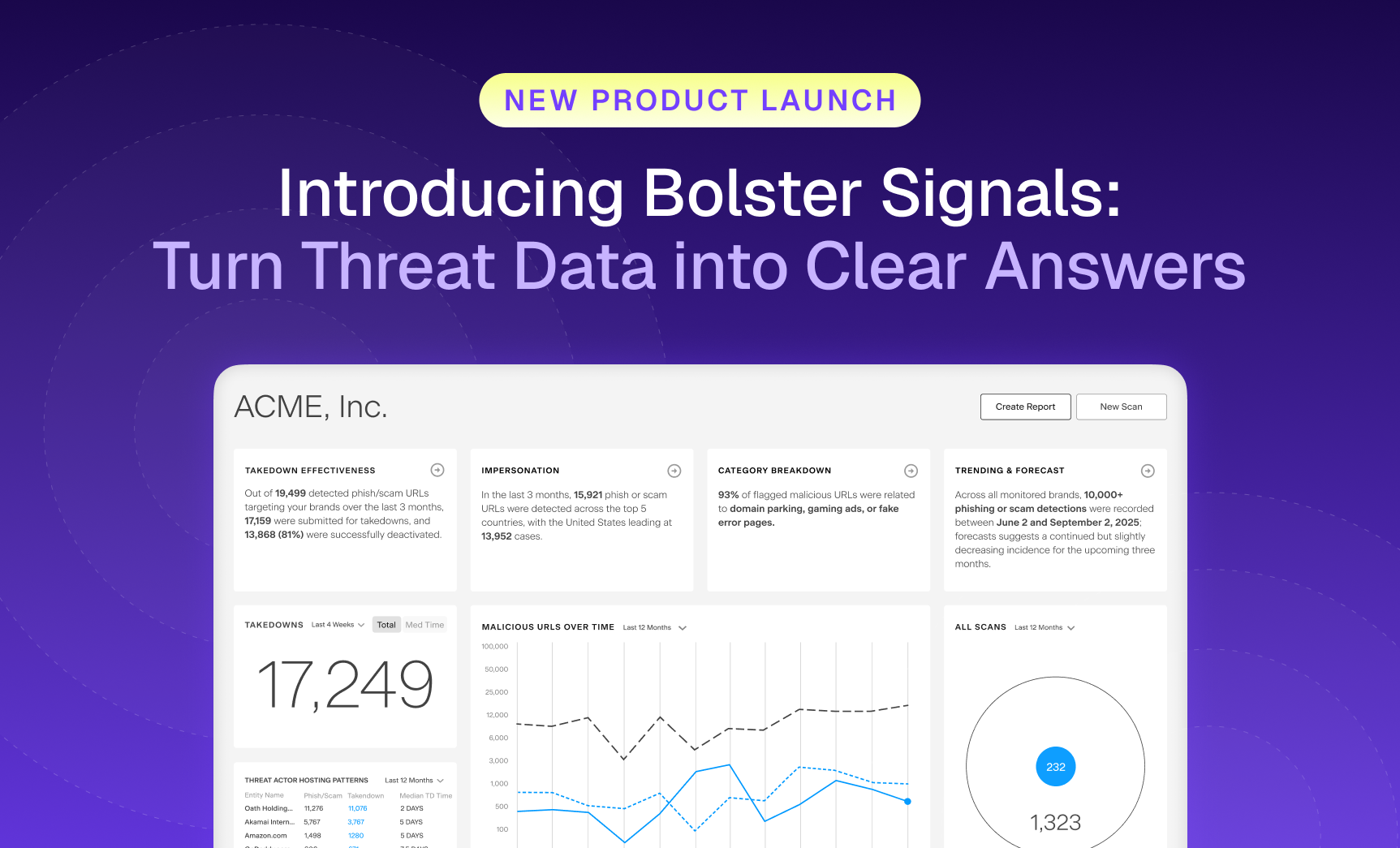
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
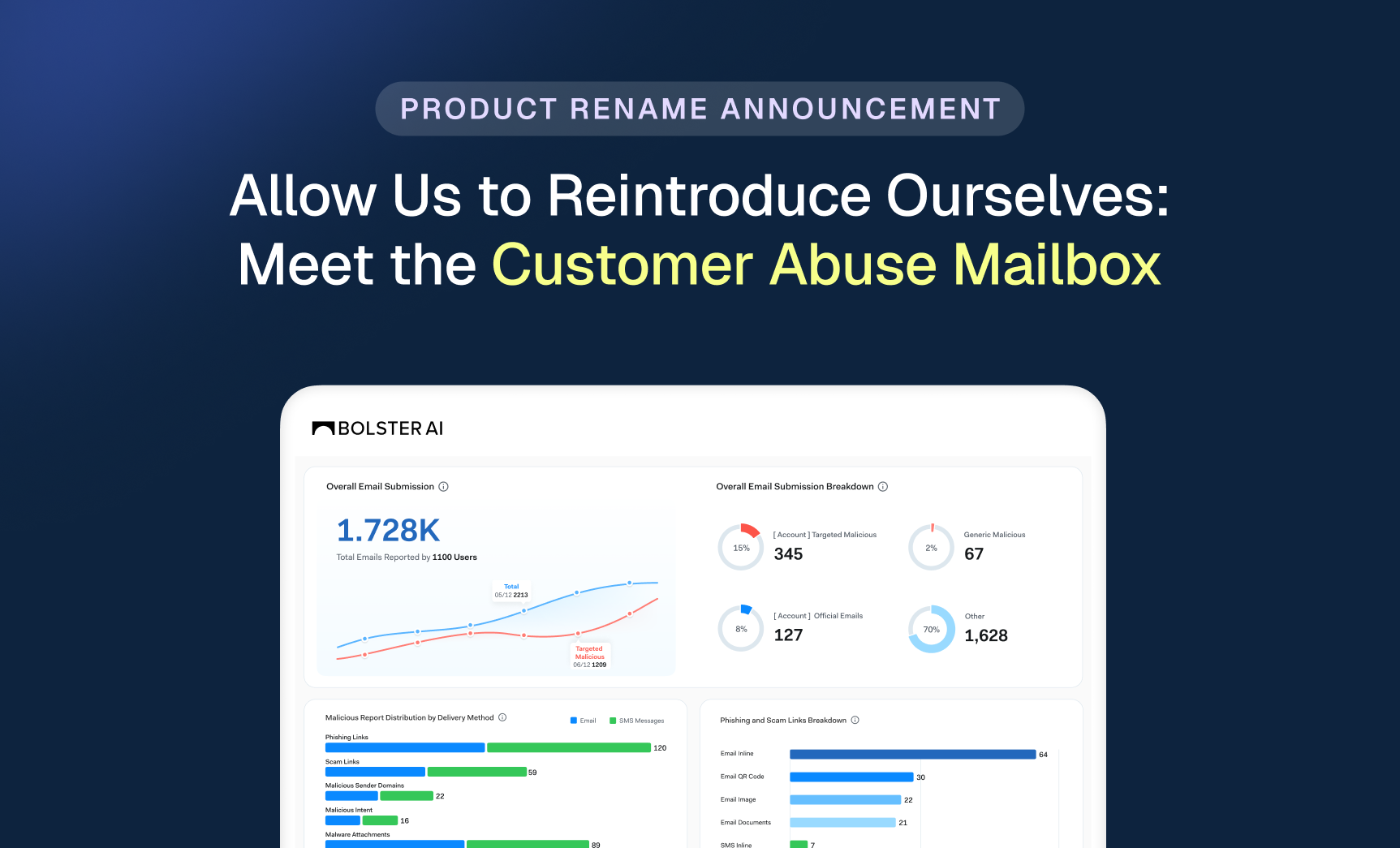
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
How to Conduct a Website Takedown In 3 Easy Steps
Malicious website domains are a headache for organizations to…
Embedded Secrets in Webpage DOMs (and How to Use this Data to Protect Your Assets)
The dangerous impact of typosquat domains, and how frequently…
Compare the Top 8 Open Source Phishing Threat Intel Feeds
Phishing threats evolve and adapt quickly. Even before one…
Top Social Media Scams to Watch Out For
Today, more than 4.6 billion people are on social…
What is Trademark Infringement and How Costly is it to Your Business?
According to a consumer survey by Stackla in 2021,…
Types of Cybercrime: A Comprehensive Guide to Uncover and Prevent Digital Attacks
The concept of using the Internet for criminal activity is…
How to File a UDRP Complaint: A Process Guide for Your Business
To build a broad-based, internationally accepted framework to deal with…
Cyber Threat Intelligence & Vulnerability Management
Threat intelligence analyzes and understands potential threats to an…
The Most Critical Domain Security Risks & Five Ways to Prevent Attacks
Security professionals are concerned about the security of their…
What You Need to Know About Domain Phishing Protection
Domain phishing attacks cause some of the biggest disruptions…
How to Remove a Typosquat Domain Targeting Your Company, Even When the Registrar Won’t Comply
Typosquat domains can damage not only an organization’s finances,…
Web Beacons: How To Effectively Use Them For Phishing Detection
Phishing attacks are the most common attack vector for…