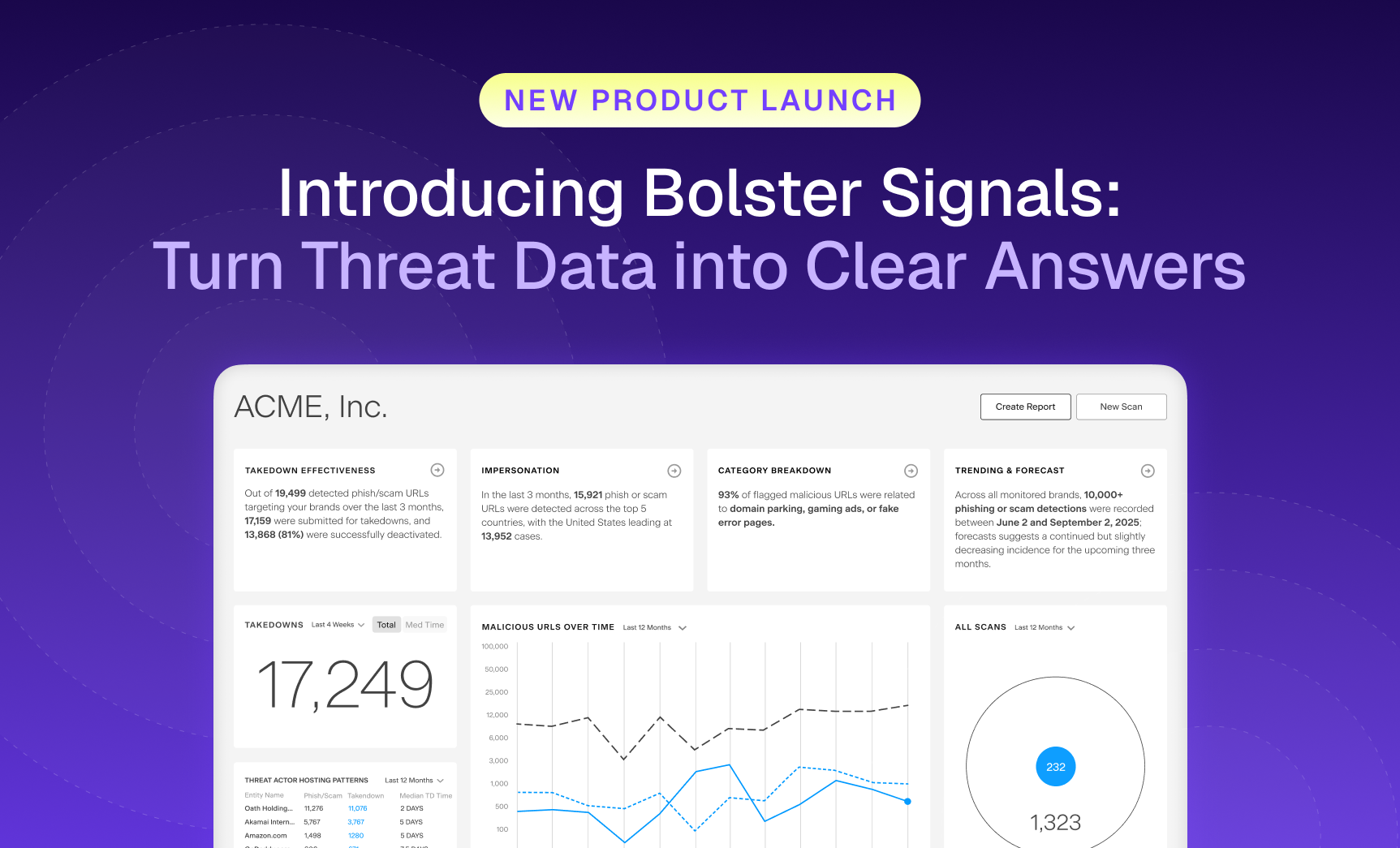
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
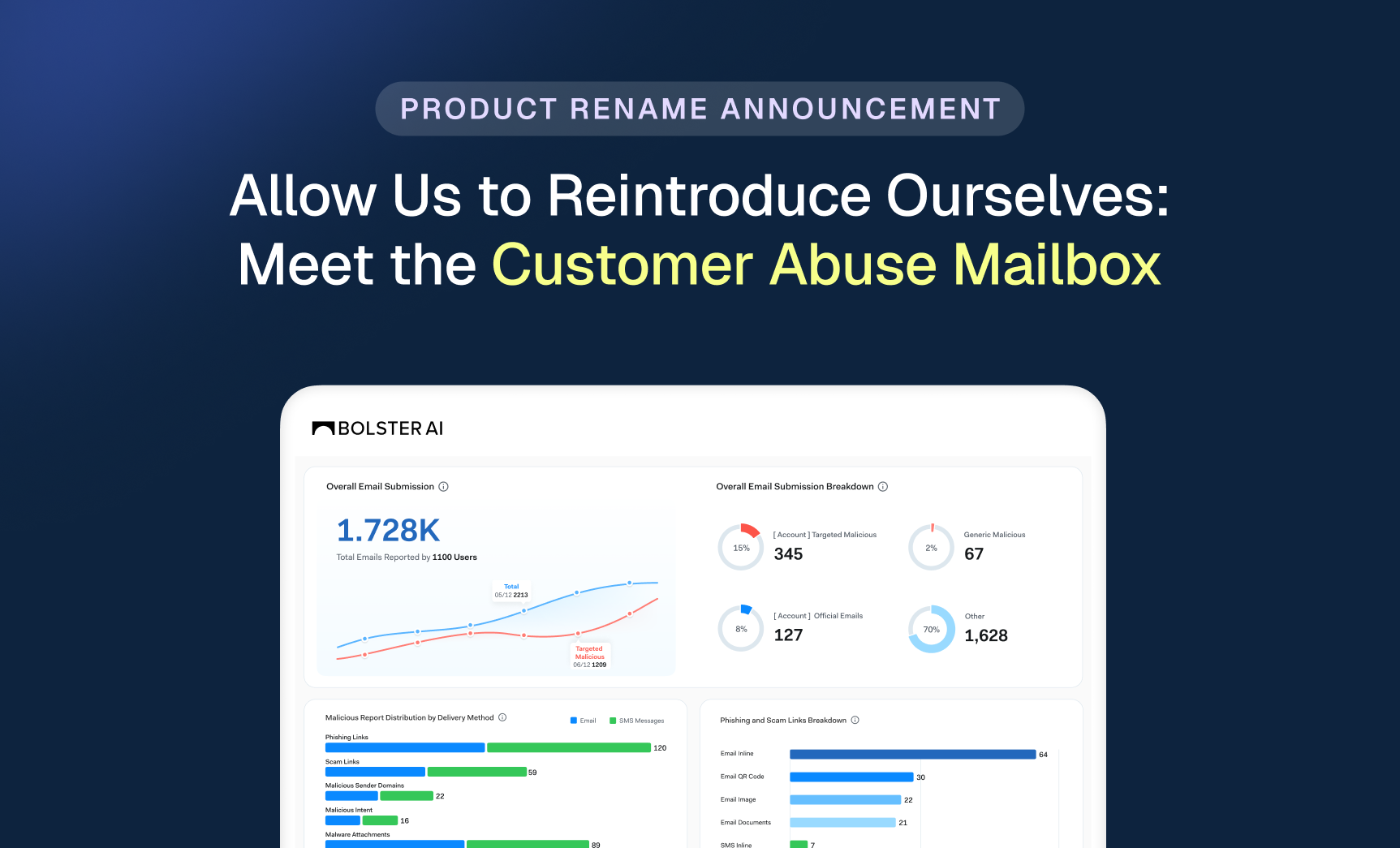
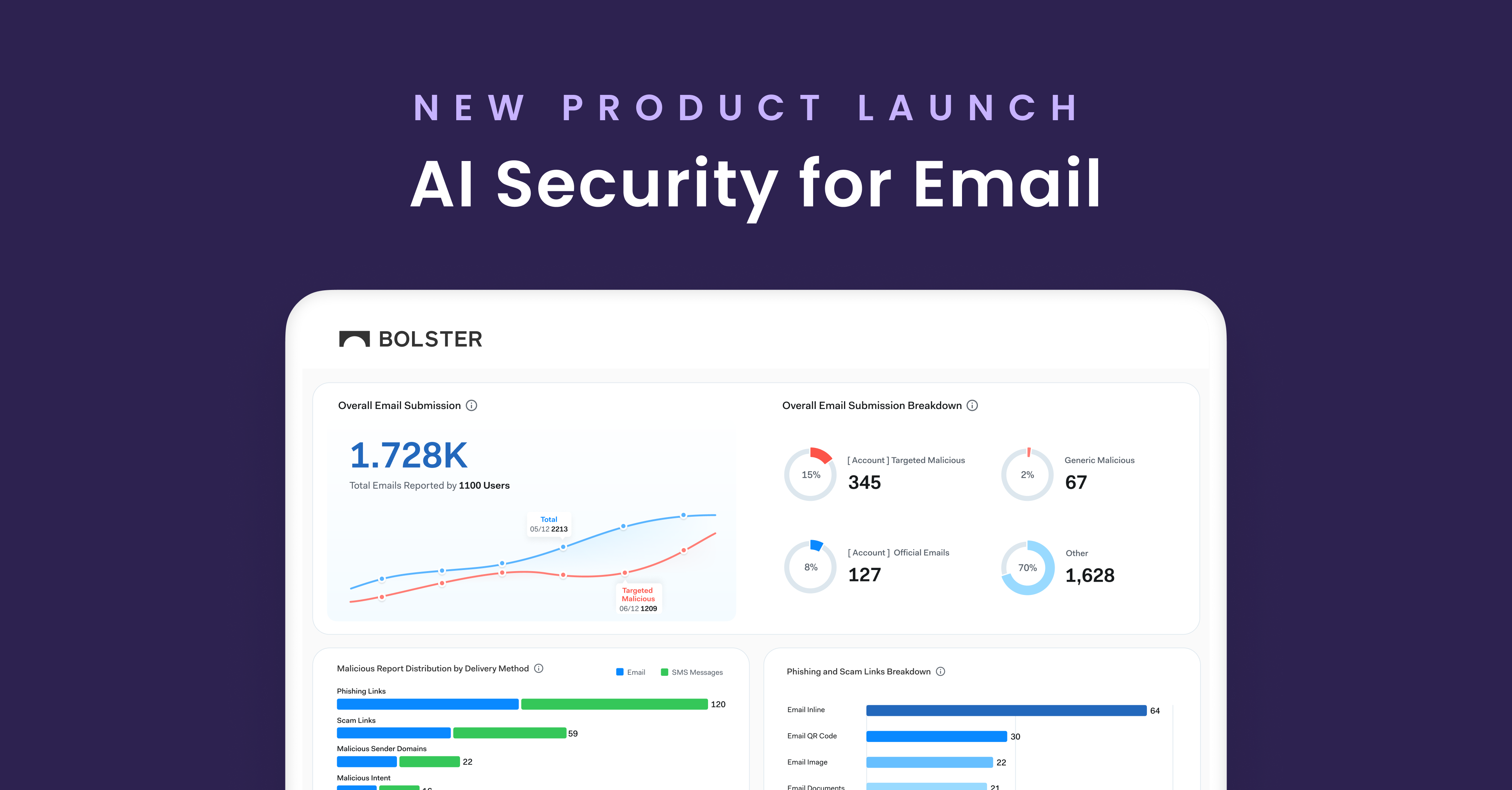
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Bolster Welcomes Rod Schultz as CEO to Lead Growth in AI-Driven Brand Security
Bolster, the leader in AI-powered brand security, is excited to…
Beyond the Perimeter: Securing Your Brand with Customer-Focused Phishing Defense
In today’s digital landscape, email continues to be a primary…
Phishing & Online Scams Targeting the 2024 Election
As the 2024 U.S. presidential election draws near with discussions,…
AI Fraud Detection in Finance: How Banks Use AI to Fight Money Laundering & More
The finance industry is in a race against increasingly sophisticated…
Credit Union Scams: How Cybercriminals Are Targeting Small Credit Unions in the US
In recent months, Bolster’s research team has identified a surge…
Understanding Domain Reputation Attacks and How to Protect Your Brand
Without even defining the term, you could probably guess that…
Spotify Email Scams to Fraudulent Parking—Catch up on This Week’s News
This week’s cyber news roundup includes some household names, healthcare…
Understanding Prepending and Its Role in Cybersecurity Attacks
Prepending involves adding data to the beginning of a string,…
In-Session Phishing is Becoming An Advanced Cybersecurity Threat
Phishing remains pretty much synonymous with “cyber attacks” as bad…
Cracking the Shield: Methods Hackers Use to Bypass MFA
Despite its apparent strength, Multi-Factor Authentication (MFA) is not immune…
Weekly News Roundup: New Senate Bill, Iranian Hackers, and Social Security Information Stolen
It’s been another busy few weeks in the world of…
From Awareness to Action: How to Avoid Government Grant Money Scams
The promise of government offers can be engaging, particularly whilst…