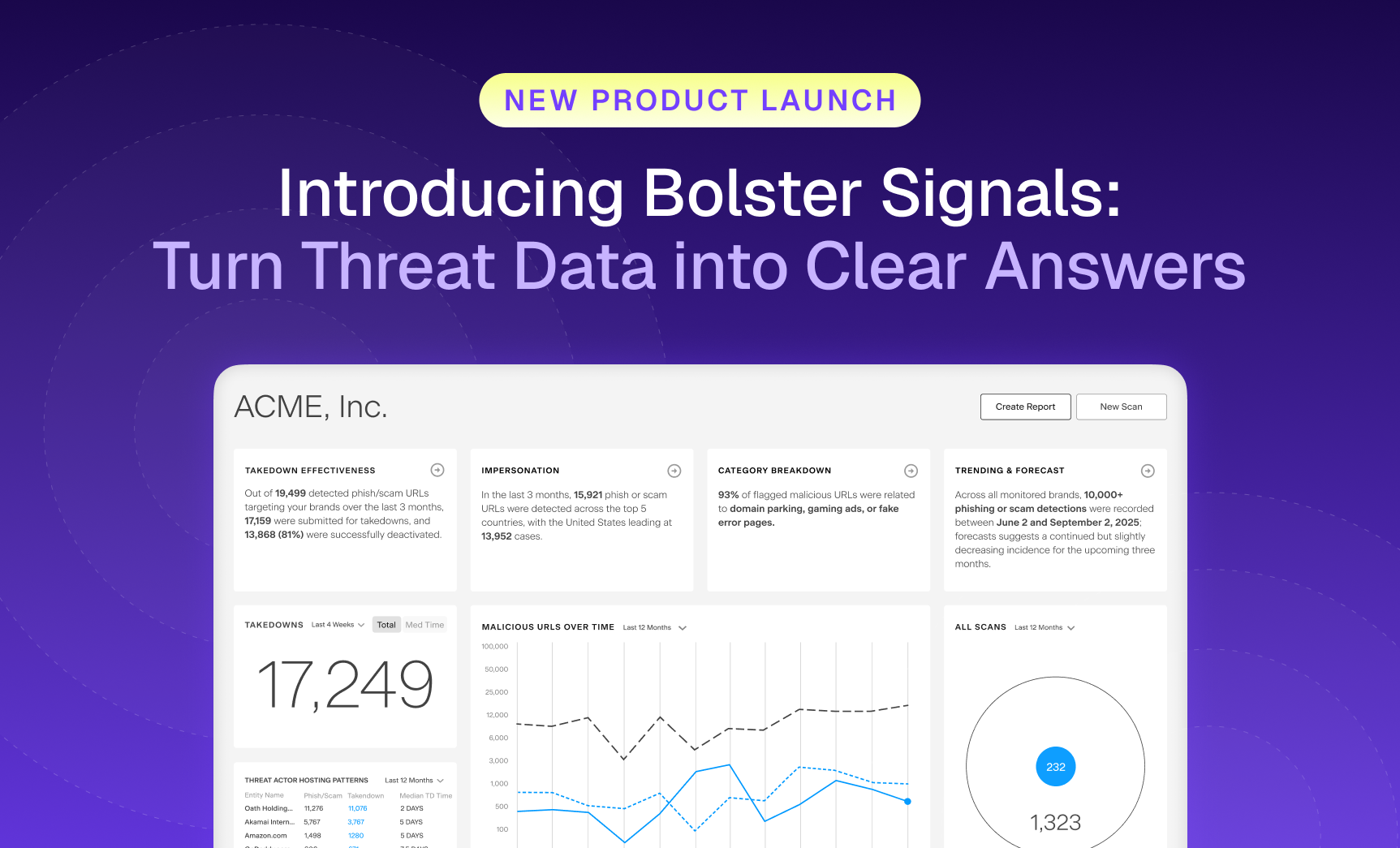
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
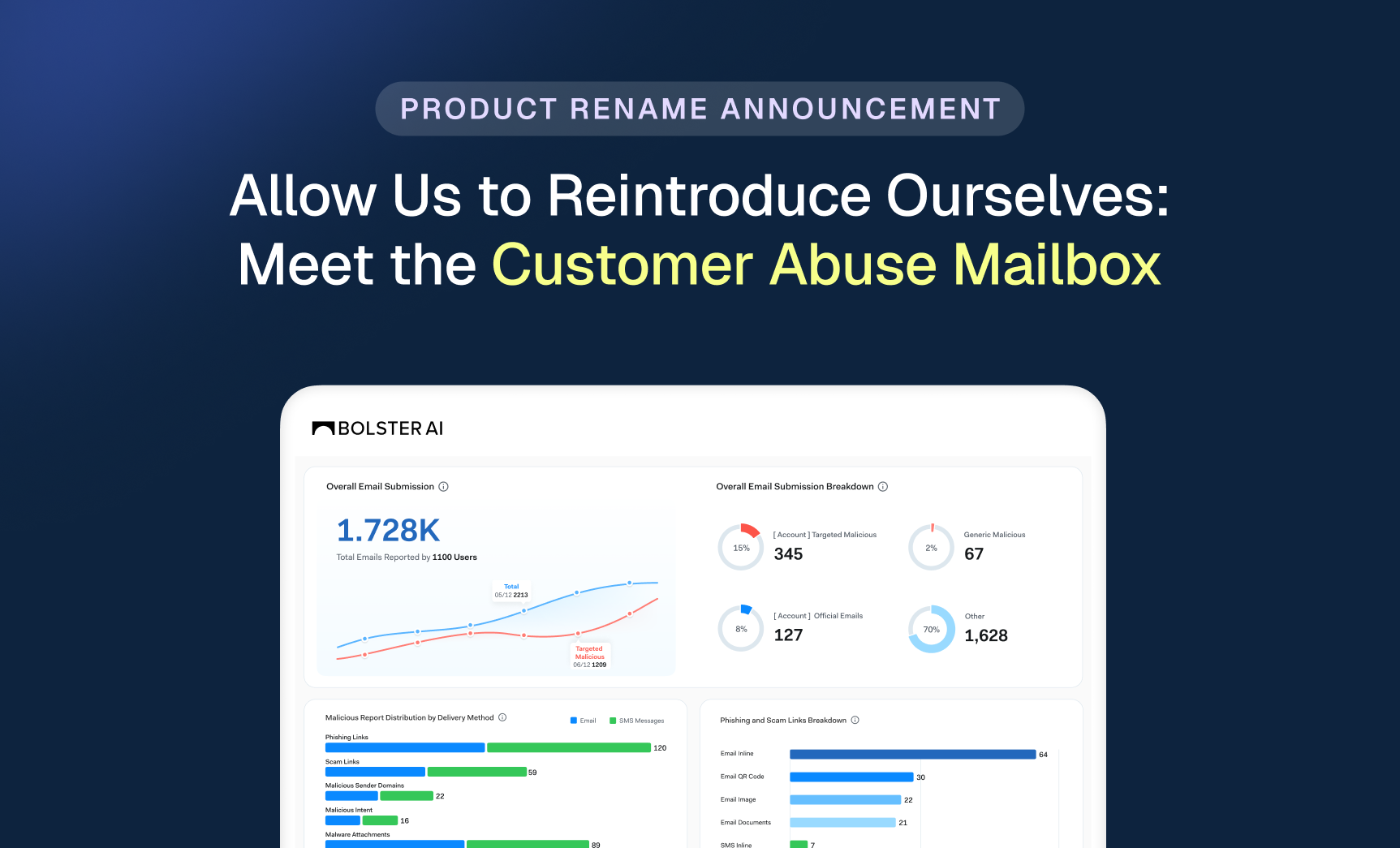
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Cracked Code, Stolen Data: The RisePro Threat on GitHub
Have you ever downloaded “free” software online? If so, you…
Weekly News Roundup: Ransomware Skyrockets, Proofpoint Phishing Emails, and More
This week, we’ve seen some big headlines in terms of…
Understanding Telegram Carding: The Dark Side of Digital Transaction
Telegram carding involves the unauthorized use of stolen credit card…
How to Find and Remove Spyware From Your iOS or Android Phone
Good news—you can protect yourself from the hidden menace of…
Browser-in-the-Browser (BitB) Phishing Attacks & Their Potential Impact on Businesses
Attackers continuously create new techniques in the ever-changing field of…
Dangers of .zip Domain Phishing & .mov Malware TLDs
New top-level domains (TLDs) like .zip and .mov have brought…
Understanding CEO Spamming and Its Threats
CEO spamming is a significant cybersecurity threat that can impact…
Personalized URL Phishing: Understanding the Threat of Email-Based Content Modification
In the ever-evolving landscape of cybersecurity threats, phishing remains one…
Proactive Defense Against BEC Attacks: How to Stay Ahead of the Scammers
Business Email Compromise (BEC) has become a significant threat to…
JavaScript-Enabled Phishing Attacks: Unmasking the Deceptive Layers of Malicious Sites
In the digital age, over 76% of businesses reported falling…
5 Ways AI is Enabling Multi-Channel Cyber Attacks (and Helping Us Combat Them)
The cyber threat landscape businesses are facing is increasingly complex…
Taylor Swift Ticket Scams: Don't Let EU Tour Phishing Nightmares Ruin Your Wildest Dreams
Fans all around Europe are clamoring to see their favorite…