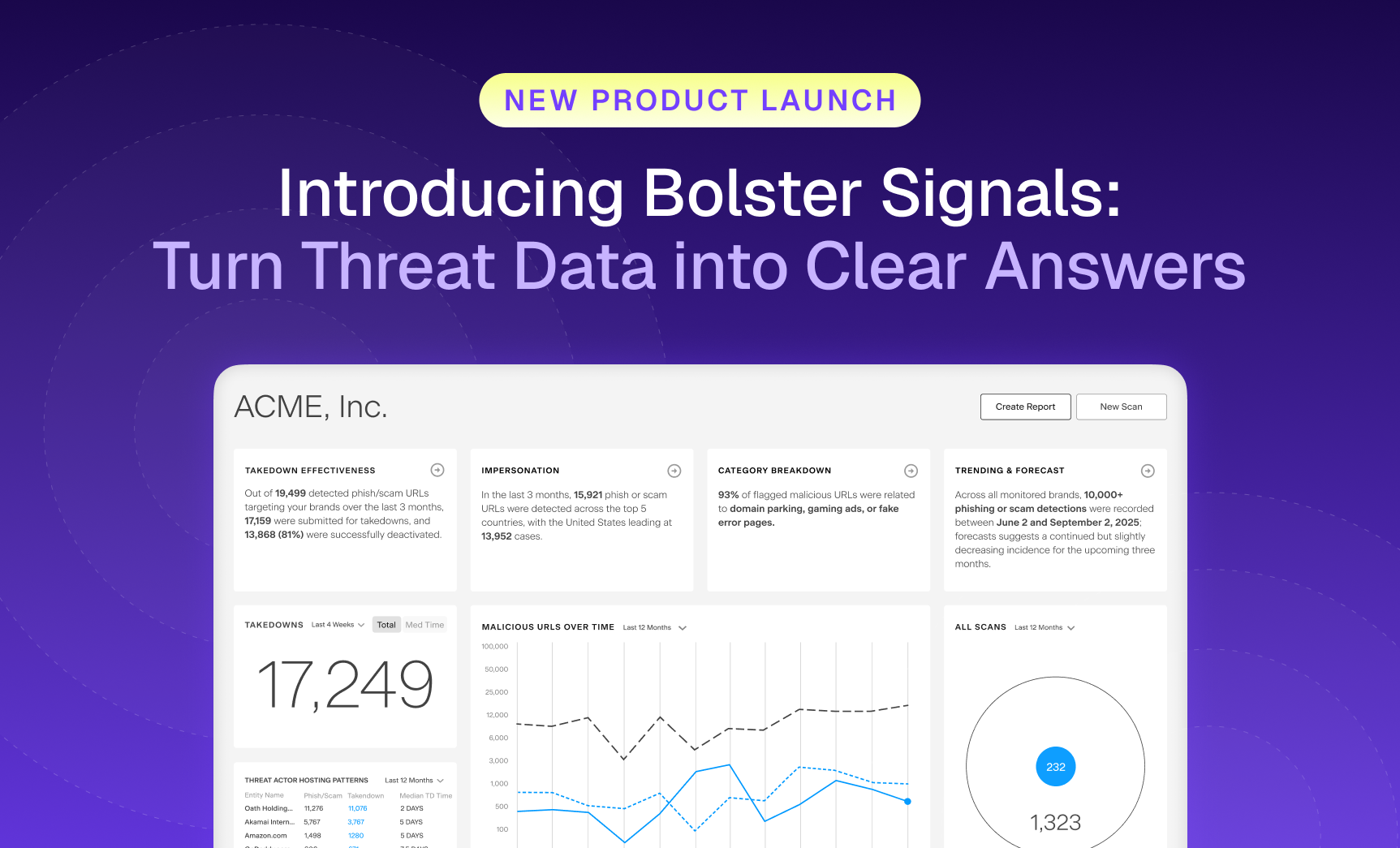
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
How to Do a Dark Web Scan: The Complete Playbook
Your organization’s credentials are probably already on the dark web; you just don’t know it yet. With 5.5 billion records exposed in 2024 and breaches.
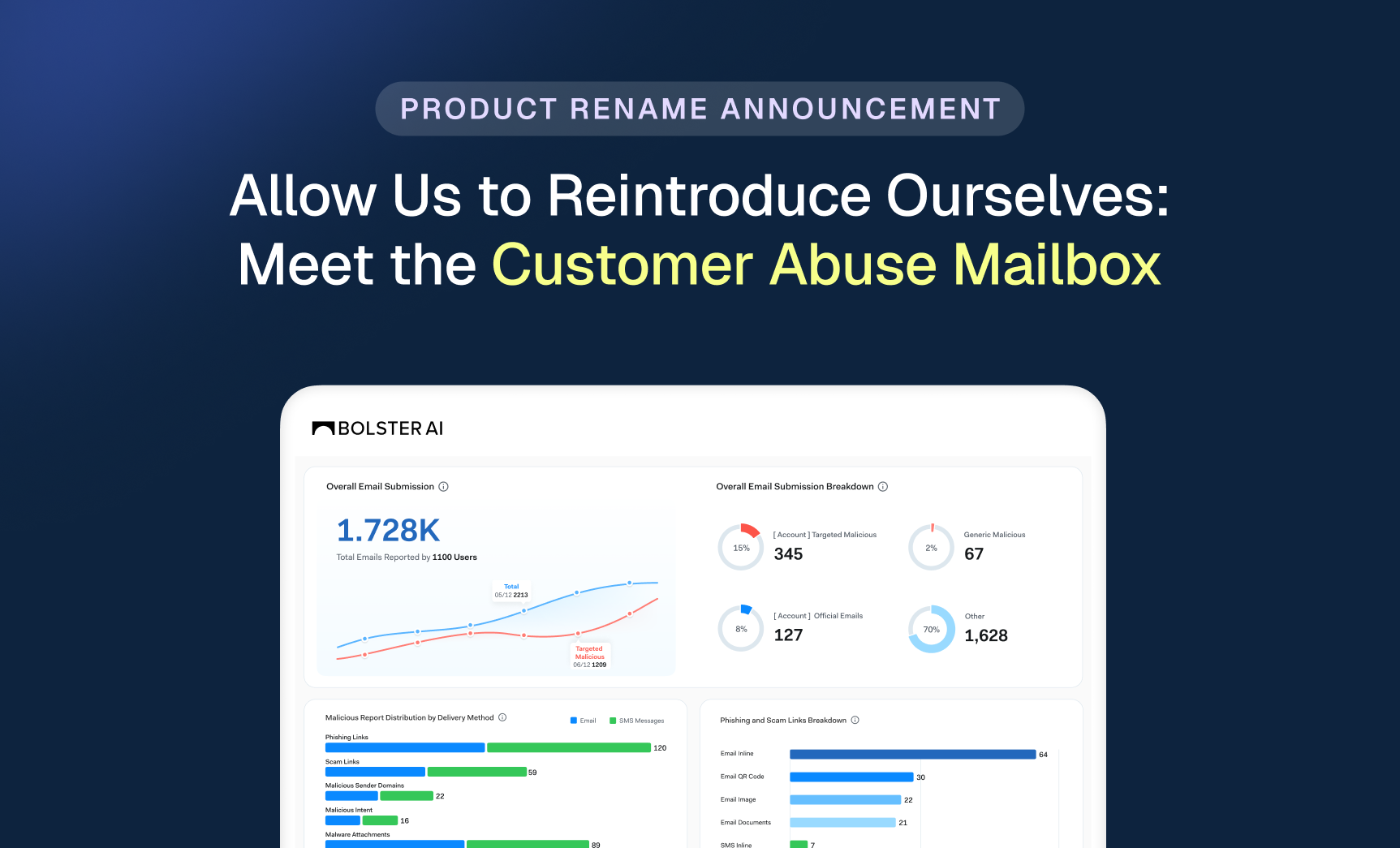
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
The Top 5 Recorded Future Competitors For 2023
Introduction Recorded Future is a traditional threat intelligence solution…
Prices for Breached Data on the Dark Web in 2022
In today’s digital age, personal information is worth more…
Zerofox Competitors and Alternatives: A Comprehensive Guide in 2023
Zerofox Competitors and Alternatives: A Comprehensive Guide In the…
4 Key Limitations of DMARC For Brand Protection
DMARC (Domain-based Message Authentication, Reporting, and Conformance) is a…
SEO Poisoning Attack Linked to 144,000 Phishing Packages
Introduction In a recent incident involving the NuGet, PyPI, and…
Can You Get Scammed on Telegram? Yes, Here's How.
Telegram promotes itself as a fast, modern cloud-based messaging platform…
Bolster Customers Achieved 278% ROI, Forrester Study Reveals
Deploying a digital risk protection platform like Bolster can…
What Is Domain Spoofing and How to Stop It
What is Domain Spoofing? Domain spoofing is a type…
24 Security Lessons to Remember This Holiday Season
Cybercriminals run rampant during the holiday season. For them,…
Top 5 Ways to Protect Customers this Holiday Season
Every year, Bolster research labs not only finds a…
Best Strategies For Stopping Business Email Compromise (BEC) Scams
Business Email Compromise scams are a surging problem that…
The Biggest Phishing Breaches of 2022 and How to Avoid them for 2023
Phishing breaches have evolved significantly in recent years. These…