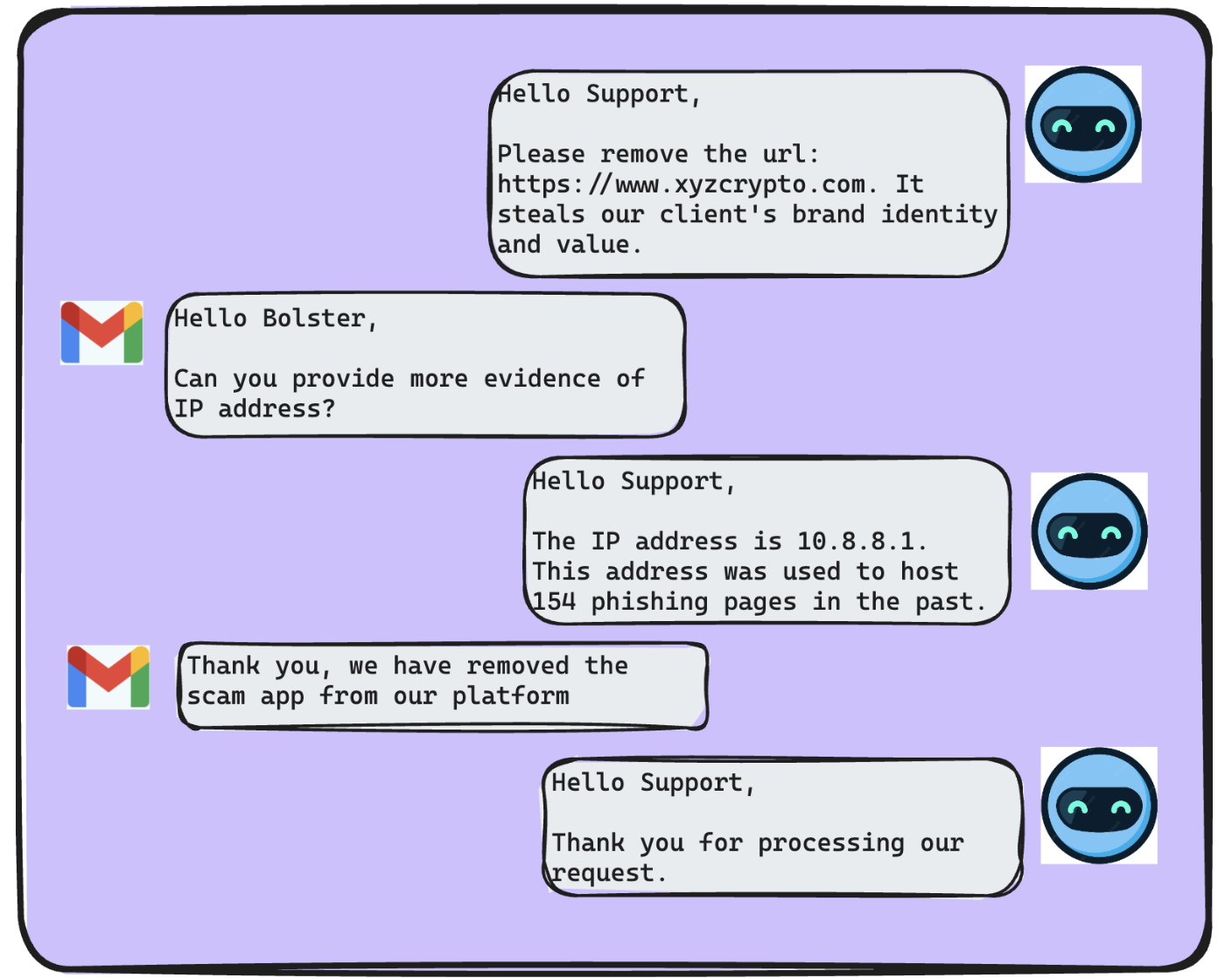
Imagine this scenario, highlighting the need for multi-channel phishing defense: …
107 results for keyword "Tips & Guides"
Online Shopping Tips to Protect Yourself During Black Friday 2023
As the holiday season swings into full gear, shoppers…
Brand Impersonation Attacks: Which Industries are Most at Risk?
In late 2022, American Express was at the center…
Automating Multi-Touch Takedowns with Large Language Models at Scale
As part of our Large Language Models at work…
5 Strategies for Reliable Protection Against BEC Scams
The recent Cloudflare 2023 Phishing Threats Report unravels many…
Empowering Brand Protection: Large Language Models and Their Role in Webpage Intent Identification for Brand Safety
Pattern recognition is a key skill that has enabled…
What is Trap Phishing? 9 Ways Your Business Can Be Impacted.
Trap phishing is a type of targeted phishing attack that…
5 Ways to Protect Your Business Against Executive Impersonation Scams
There’s no doubt social media cyber risk attacks are…
What Are Executive Impersonation Attacks, and What Do They Look Like?
Cybercriminals keep coming up with new methods to deceive…
Top 4 Features of a Dark Web Monitoring Tool
The term “dark web” often gives off an ominous…
The Power of Automated Domain Monitoring
Today, business owners around the world understand that digital…
The 8 Most Common Anti-Phishing Solutions for Your Business to Utilize
Phishing is one of the primary threats to businesses…