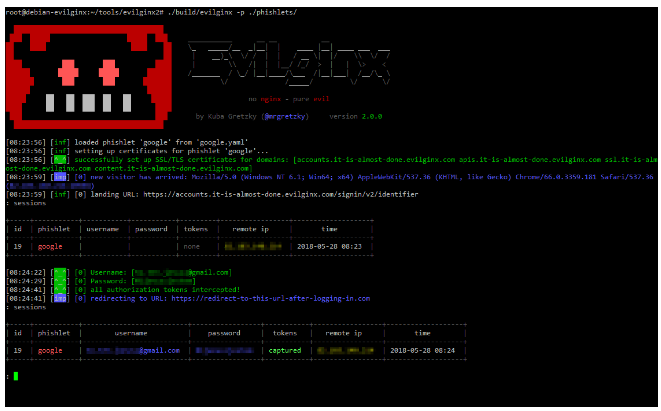
Imagine clicking on what looks like your bank’s login page.…
82 results for keyword "Research Labs"
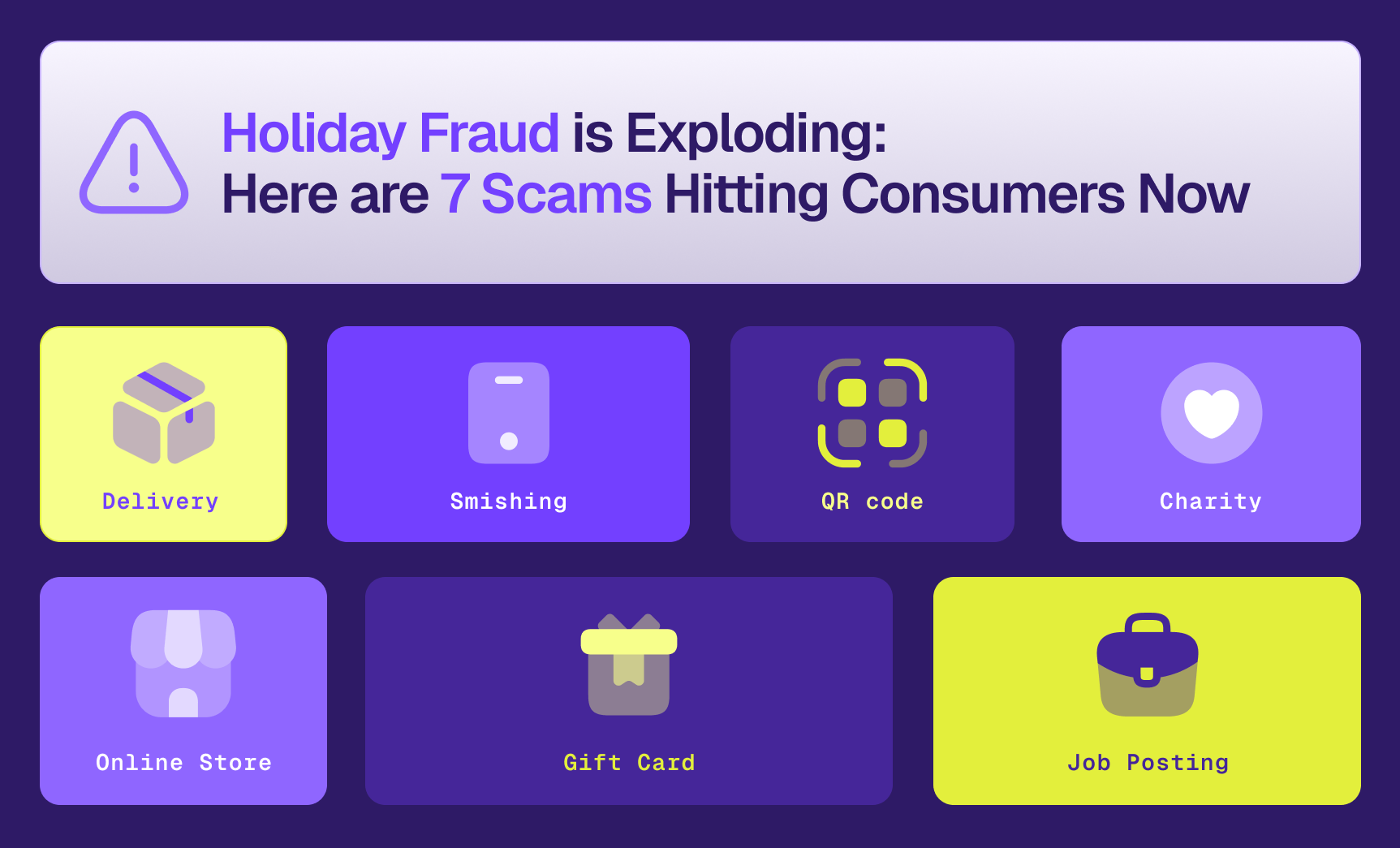
Holiday Fraud is Exploding: Here Are the 7 Scams Hitting Consumers Now
Spoiler: They’re more sophisticated, more convincing, and harder to spot than ever. …
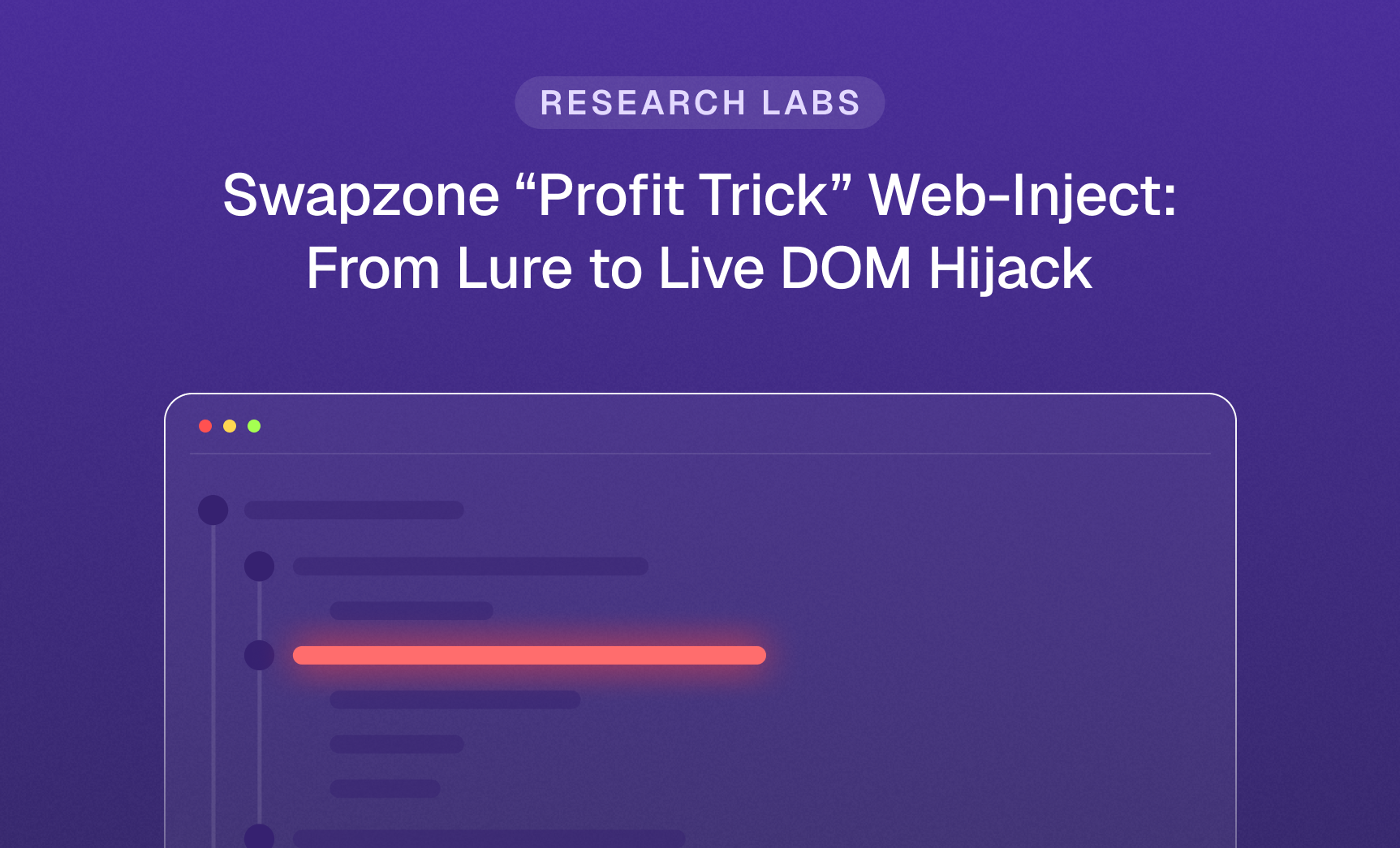
Swapzone “Profit Trick” Web-Inject: From Lure to Live DOM Hijack
Introduction At Bolster’s Threat Intelligence Lab, we recently investigated a…
Conditional Phishing and Beyond: The Hidden Triggers in Modern Cyber Attacks
Introduction Phishing has always been about deception, but in recent…
Image Tokenization: How Vision Transformers See the World
Convolutional Neural Networks (CNNs) have dominated computer vision for the…
The ROI of Brand Protection: Why Safeguarding Your Brand Pays Off
Brand abuse isn’t just a nuisance—it’s a threat to your…
Quantum Computing and the Future of Hosting: Why It’s Time to Prepare Now
Google, AWS, and IBM aren’t just dabbling in quantum—they’re investing…
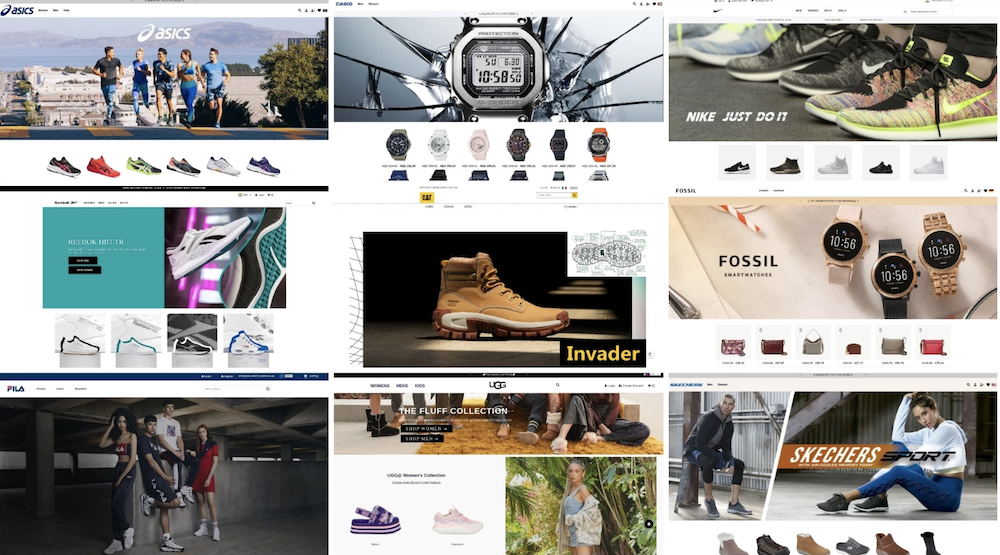
How a Massive Brand Impersonation Scam Campaign Targeted Popular Apparel Brands
Back in 2023, Bolster’s threat research team uncovered a widespread…
Large Language Models for Cybersecurity: The Role of LLMs in Threat Hunting
Organizations are turning to artificial intelligence (AI) and, more specifically,…
Social Engineering: The Gateway to Phishing Attacks
Cybersecurity threats are constant, and social engineering is one of…
AI’s influence on stock market predictions & using AI in your investing strategy
Artificial intelligence has found its place in financial markets, bringing…